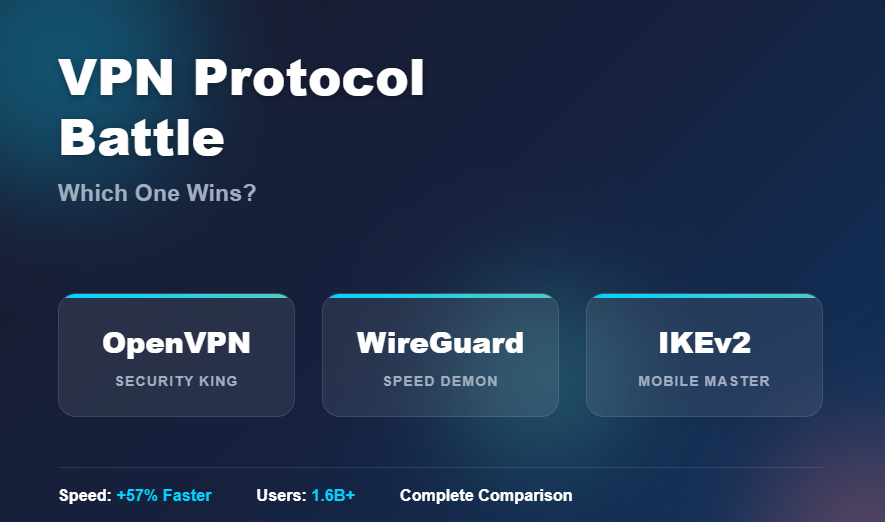
VPN Protocol Comparison – OpenVPN vs WireGuard vs IKEv2: Which Protocol Wins in 2025?
According to recent industry analysis, the global VPN market reached over 1.6 billion users in 2024, yet most don’t understand the protocols powering their connections. Your VPN protocol determines everything from connection speed to security strength and network stability. The three dominant protocols – OpenVPN, WireGuard, and IKEv2 – each offer distinct advantages, but choosing…