Double VPN vs Tor Over VPN – Speed & Security Trade-offs
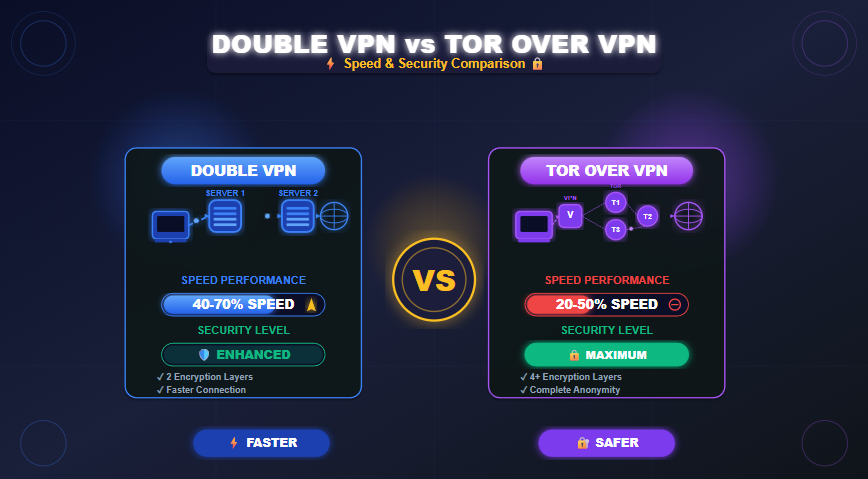
According to industry data from 2024, VPN latency measurements showed dramatic variations across different connection types, with standard single-hop VPNs recording download latency as low as 5.4 milliseconds. However, multi-hop configurations introduce significantly different performance characteristics. When you’re considering advanced privacy solutions beyond standard VPN encryption, two technologies dominate the conversation – Double VPN and Tor over VPN. Both route your traffic through multiple servers, but they achieve this protection through fundamentally different architectures with distinct trade-offs.
Understanding how these technologies impact your connection speed and security posture helps you make informed decisions about which solution matches your specific privacy requirements.
What Is Double VPN and How Does It Work
Double VPN technology routes your internet traffic through two separate VPN servers instead of one, encrypting your data twice before it reaches its final destination. This process is also known as multi-hop VPN or VPN cascading.
When you connect to a Double VPN configuration, your device first establishes an encrypted connection to the initial VPN server. This server then creates a separate encrypted tunnel to a second VPN server, typically located in a different country. Your data undergoes encryption at each stage, creating two distinct layers of protection.
The second server has no information about your original IP address because the first server already masked it. Similarly, anyone monitoring the first server cannot see your final destination because the second server handles that routing. Research from Cloudflare’s networking analysis shows that VPNs can increase latency by introducing extra travel time for requests and responses through additional server hops.
The Multi-Hop Architecture Explained
Multi-hop VPN services work through server cascading – your traffic passes through a chain of VPN servers before exiting to the public internet. Some providers offer pre-configured Double VPN server pairs, while others allow you to manually select your routing path.
Modern implementations use different approaches. Some services encrypt data twice, once at each server. Others use a server-proxy combination where the VPN encrypts traffic and sends it to a server, which then masks your IP and forwards it to a proxy for additional IP masking without redundant encryption.
According to technical documentation from CISA’s encryption guidance, modern encryption standards like AES-256 provide robust security that remains effective even with quantum computing considerations for decades to come.
Key Benefits of Double VPN Technology
Double VPN configurations deliver several security advantages for users with elevated privacy requirements:
Enhanced IP masking – Your actual IP address remains hidden from the exit server, creating an additional anonymity layer similar to how Tor conceals data between entry and exit nodes.
Multiple jurisdiction protection – Routing through servers in different countries shields you from single-government jurisdiction over your data. Even if one country’s authorities could access one server, they couldn’t connect your traffic to your identity without accessing both servers.
Redundant encryption layers – If one encryption layer were somehow compromised, the second layer continues protecting your data. This redundancy significantly increases the difficulty of intercepting and decrypting your communications.
Understanding Tor Over VPN Configuration
Tor over VPN combines two distinct privacy technologies by routing your encrypted VPN traffic through the Tor network. This configuration means your internet service provider sees you connecting to a VPN, while the Tor network receives encrypted traffic from the VPN server rather than your actual IP address.
The Tor network routes your internet traffic through at least three randomly selected volunteer-run servers – called nodes or relays – located worldwide. Each node strips away one encryption layer and forwards your traffic to the next relay without knowing both your origin and destination.
According to security analysis from Top10VPN, Tor’s routing method effectively disconnects your true IP address from your online activity through its decentralized network architecture, though this creates significant speed trade-offs.
How Tor’s Onion Routing Functions
When you use Tor, your traffic receives multiple layers of encryption – hence the “onion” metaphor. The entry node knows your IP address but not your destination. Middle relays know neither. The exit node sees your destination but not your origin.
Data travels approximately 200 kilometers per millisecond through fiber optic cables. For latency, you must account for travel time twice – once to reach the remote host and once for the response. Real-world achievable latency is approximately 1 millisecond for every 100 kilometers of distance between hosts, according to performance data from IVPN’s speed analysis.
Each additional hop introduces processing delays, encryption overhead, and routing inefficiencies. With Tor requiring three or more hops through volunteer servers of varying capacity, speed impacts become substantial.
Tor Over VPN vs VPN Over Tor
These configurations differ fundamentally in what they hide from whom. Tor over VPN means you connect to your VPN first, then access Tor through that encrypted connection. Your ISP sees VPN traffic but not Tor usage. The Tor entry node sees your VPN’s IP address rather than your real one.
VPN over Tor means you connect to Tor first, then route that traffic through a VPN. Your ISP knows you use Tor. The VPN provider cannot see your real IP address because Tor masked it. However, the VPN exit server sees your final destination traffic if you access non-HTTPS sites.
Security experts documented in comprehensive privacy research that combining these tools isn’t a panacea – it can introduce new attack surfaces. In some setups, you may end up worse off than using Tor alone if the VPN’s visibility or misconfiguration deanonymizes your traffic.
Double VPN vs Tor Over VPN – Speed Comparison
Speed performance represents the most significant practical difference between these two technologies. Testing data reveals substantial variations in how each approach impacts connection speeds and latency.
Standard VPNs typically reduce download speeds by 10-20% compared to unencrypted connections. This represents normal overhead from encryption processing and the additional routing hop. Research from NordVPN’s performance testing shows that well-configured premium VPNs minimize this speed reduction, often with no noticeable change in loading times or streaming quality.
Double VPN Performance Impact
Double VPN configurations typically reduce speeds by 30-60% compared to standard single-hop connections. This performance hit stems from multiple factors working in combination.
Your data travels through two distant servers rather than one, doubling the physical distance covered. Each server adds its own processing overhead for encryption, decryption, and routing. Server load on both hops affects performance – if either server experiences congestion, your entire connection suffers.
According to VPN performance statistics from 2024, latency measurements across various providers showed significant variations. While single-hop connections achieved latencies as low as 5.4 milliseconds for hide.me, multi-hop configurations introduce substantially higher delays.
Despite these limitations, Double VPN connections remain viable for most regular internet activities. You can browse websites, send emails, and stream content at standard definition. High-bandwidth activities like 4K streaming or large file transfers will show noticeable slowdowns.
Tor Over VPN Speed Characteristics
Tor over VPN creates the most significant speed reduction among privacy technologies. Users typically experience 50-80% speed decreases compared to unencrypted connections, with some scenarios showing even greater impact.
The Tor network itself introduces substantial latency because your data bounces through at least three volunteer-run servers of varying capacity and geographic distribution. Adding VPN encryption before entering this already-slow network compounds the performance issues.
Testing documented by multiple security researchers consistently shows Tor can be noticeably slower than VPNs because internet traffic routes through multiple volunteer-run servers. This extra routing makes pages, photos, and videos take longer to load, especially when fewer people help run the network.
Real-time applications suffer most severely. Video calls become practically impossible with the added latency. Online gaming experiences severe lag that makes competitive play unfeasible. Even website browsing feels sluggish with 3-5 second page load delays becoming common.
When Speed Matters Most
Understanding your use case determines which technology you should implement. For activities demanding high speeds – streaming video content, downloading large files, video conferencing, or online gaming – standard single-hop VPNs provide the best balance.
Double VPN works acceptably for general browsing, email, messaging, and standard-definition video when you need elevated security. The 30-60% speed reduction remains manageable for these activities.
Tor over VPN should be reserved exclusively for situations where maximum anonymity outweighs all speed concerns. Sensitive communications, whistleblowing, accessing blocked content in oppressive regimes, or any scenario where exposure could create physical danger justifies the severe speed penalty.
Security Analysis – Double VPN Protection
Double VPN delivers measurable security improvements over standard single-hop VPN connections through its redundant architecture. These benefits matter most for users facing sophisticated adversaries or handling highly sensitive information.
The primary security advantage comes from compartmentalized trust. No single server operator knows both your identity and your browsing destination. The first server sees your real IP address but only knows you’re connecting to another VPN server. The second server sees your final destination but cannot link it back to your actual IP.
Encryption Layer Redundancy
Double encryption provides a safety net against cryptographic failures. While modern encryption algorithms like AES-256 are considered unbreakable with current technology, the redundant layers guard against implementation flaws or future vulnerabilities.
According to CISA’s encryption standards documentation, comprehensive encryption using cryptographic algorithms that are ordinarily accepted by cybersecurity experts provides confidentiality and integrity protections against currently known techniques and reasonably foreseeable computing power.
If researchers discovered a weakness in one encryption protocol, the second layer maintains protection. This proves particularly valuable given the extended timeframes involved in patching security vulnerabilities across large networks.
Jurisdictional Distribution Benefits
Routing through servers in different legal jurisdictions creates meaningful obstacles for surveillance efforts. An adversary would need to simultaneously compromise or gain legal access to servers in multiple countries – a substantially more difficult undertaking than monitoring a single connection point.
Different countries have varying data retention laws, surveillance capabilities, and international cooperation agreements. This geographic diversity makes comprehensive traffic correlation extremely challenging even for well-resourced state actors.
For journalists, activists, or business professionals operating in restrictive environments, this jurisdictional distribution represents a critical security layer. Understanding VPN encryption standards and their implementation helps users evaluate which providers offer robust protection.
Limitations of Double VPN Security
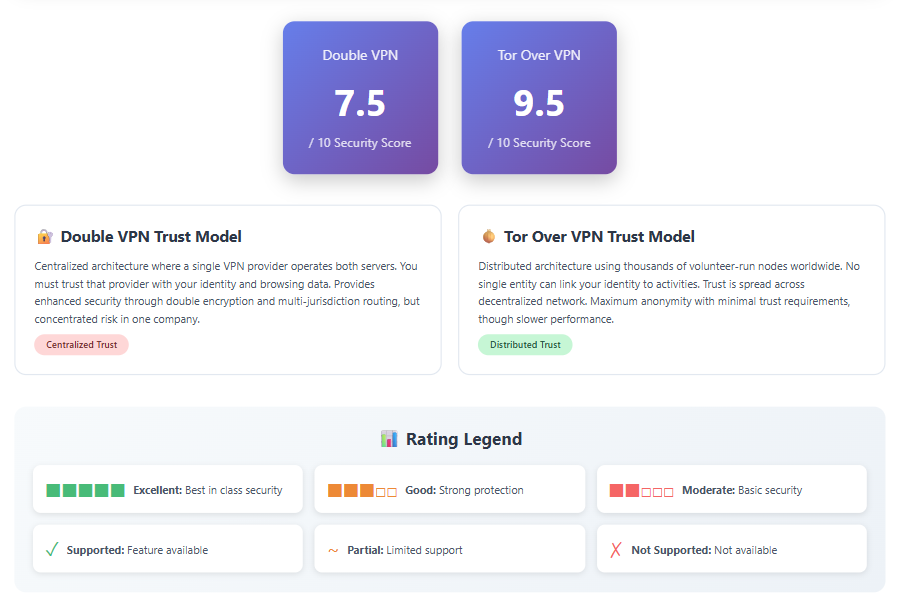
Double VPN does not provide anonymity equivalent to Tor. Your VPN provider still knows your real IP address because you connected directly to their first server. If that provider logs connections or responds to government data requests, your identity remains discoverable.
The security depends entirely on trusting your VPN provider’s no-logs policy and security practices. You’re concentrating trust in a single company operating both servers in the chain, rather than distributing that trust across independent entities like Tor does.
Performance testing from cybersecurity research shows that speed drops by 30-60% compared to single-hop connections. This creates practical trade-offs between security and usability that users must carefully weigh.
Tor Over VPN Security Advantages
Tor over VPN combines the encryption of commercial VPN services with Tor’s decentralized anonymity network, creating the strongest available privacy protection for civilian use. This configuration delivers genuine anonymity that even well-resourced adversaries struggle to compromise.
The layered approach means no single entity can link your real identity to your online activities. Your VPN provider sees your IP but not your final destination or browsing activities. The Tor entry node sees your VPN’s IP rather than your real one. The exit node sees your destination but has no information about your origin.
Decentralized Trust Model
Tor’s fundamental security advantage comes from distributing trust across thousands of volunteer-operated nodes worldwide. Unlike centralized VPN services where a single company controls all servers, Tor relies on a network where no individual operator can monitor complete traffic patterns.
According to detailed privacy analysis, the Tor network encrypts and sends traffic through a series of volunteer-run nodes located worldwide, with each node only able to decrypt one layer of encryption and know where traffic came from or where it’s going.
This architecture prevents traffic correlation attacks that could link your activities to your identity. An adversary would need to simultaneously control the entry node, middle relays, and exit node in your specific circuit to deanonymize you – a scenario Tor’s random routing makes extremely improbable.
Hiding VPN Usage From ISPs
In countries with internet censorship or surveillance, even using a VPN can attract unwanted attention from authorities. Tor over VPN solves this problem by hiding your VPN usage from your internet service provider.
Your ISP sees only that you’re connecting to Tor – it cannot identify which VPN service you’re using or any details about your encrypted traffic. In jurisdictions where VPN usage is restricted or monitored, this provides an additional protective layer.
Some oppressive regimes have attempted to block Tor by maintaining lists of known Tor entry nodes. A VPN connection first allows you to bypass these blocks because the Tor network sees only your VPN server’s IP address connecting to the Tor entry node.
Protection Against Exit Node Monitoring
Tor exit nodes represent a potential vulnerability where malicious operators could monitor unencrypted traffic. While HTTPS protects most modern web traffic, the exit node operator could still observe which websites you visit and potentially intercept any remaining unencrypted data.
Using Tor over VPN doesn’t eliminate this risk entirely, but it disconnects any observed traffic from your real identity. Even if an adversary operates a malicious exit node and captures your data, they cannot link it back to your actual IP address or identity because the Tor network obscured that information.
Practical Use Cases for Each Technology
Choosing between Double VPN and Tor over VPN depends heavily on your specific security requirements, threat model, and acceptable performance trade-offs. Different scenarios call for different approaches.
When to Use Double VPN
Double VPN proves ideal for users who need enhanced security without the severe performance penalties of Tor. Several specific scenarios benefit from this configuration:
Business travelers in hostile environments face elevated risks when accessing corporate systems from hotels or public WiFi in countries known for cyber espionage. Double VPN provides strong protection against local adversaries while maintaining adequate speeds for video conferences and file transfers.
Financial professionals handling sensitive transactions require protection that exceeds standard VPN security without the sluggish performance that would disrupt trading platforms or real-time market data feeds. The 30-60% speed reduction remains acceptable while providing stronger encryption.
Journalists conducting routine research on sensitive topics benefit from Double VPN’s enhanced privacy for preliminary investigations. When research escalates to high-risk source communications, transitioning to Tor over VPN becomes advisable.
According to technical implementation guidance, multi-hop connections create double encryption and mask your IP address from the exit server while routing traffic through multiple jurisdictions.
When to Use Tor Over VPN
Tor over VPN represents the highest level of privacy protection available to civilians, but its severe performance limitations mean it should be reserved for situations where anonymity outweighs all other considerations:
Whistleblowers communicating with journalists need absolute protection that prevents powerful adversaries from identifying them. The speed penalty becomes irrelevant when exposure could result in prosecution or physical danger. Documents can be uploaded slowly, and communications can happen asynchronously.
Political activists in authoritarian regimes organizing demonstrations or sharing information face imprisonment or worse if identified. Tor over VPN provides the strongest available protection against state surveillance apparatus, even if browsing speeds become frustratingly slow.
Security researchers investigating criminal infrastructure need genuine anonymity to avoid retaliation. When examining dark web marketplaces, botnets, or hacking forums, the connection between their research activities and real identity must be completely severed.
Accessing censored information in oppressive countries often requires bypassing sophisticated Deep Packet Inspection systems. Tor over VPN defeats these censorship technologies while protecting users from punishment for circumventing government controls.
Situations Where Standard VPN Suffices
Most users don’t need Double VPN or Tor over VPN for everyday privacy protection. A reliable single-hop VPN provides adequate security for common scenarios:
Protecting your data on public WiFi networks in cafes or airports only requires standard VPN encryption. The threat model involves opportunistic hackers, not targeted surveillance operations.
Streaming geo-restricted content or bypassing regional blocks works best with single-hop VPNs because they provide optimal speeds. Entertainment applications don’t warrant the performance sacrifices of multi-hop configurations.
General privacy from ISP monitoring, advertiser tracking, and routine data collection needs only single-hop VPN protection. These commercial data harvesting operations don’t employ sophisticated traffic analysis that would penetrate standard VPN encryption.
Configuration and Setup Requirements
Implementing these privacy technologies requires different levels of technical knowledge and infrastructure. Understanding the setup complexity helps you determine which approach fits your capabilities.
Setting Up Double VPN
Most major VPN providers now offer Double VPN functionality with pre-configured server pairs. These implementations require no technical knowledge beyond selecting the Double VPN option in your VPN client application.
Premium services typically provide 20-30 pre-configured Double VPN server combinations. You simply choose which country pair you want – such as Netherlands to Switzerland or Singapore to Canada – and connect with a single click.
The provider handles all technical aspects of routing your traffic through both servers and maintaining the encrypted tunnels between them. This plug-and-play simplicity makes Double VPN accessible to non-technical users who need enhanced security.
Some advanced VPN services allow custom multi-hop configurations where you manually select both servers in the chain. This provides greater flexibility but requires understanding network topology and potential vulnerabilities in different routing paths.
Implementing Tor Over VPN
Tor over VPN setup follows a straightforward two-step process. First, connect to your VPN service as normal by launching the VPN client and selecting a server. Verify the VPN connection is active and your IP address has changed using any IP checking website.
Second, launch the Tor Browser while your VPN connection remains active. The Tor Browser automatically routes all its traffic through the Tor network. Your VPN connection ensures all Tor traffic is encrypted before entering the Tor network.
No additional configuration is necessary. The two systems work independently – the VPN encrypts and routes all traffic from your computer, while the Tor Browser adds its own layers of Tor routing on top of that foundation.
Some VPN providers offer built-in Tor integration through “Onion over VPN” features. These implementations automatically route VPN traffic through Tor without requiring the separate Tor Browser, though security researchers sometimes question whether these implementations provide equivalent protection to running the technologies independently.
Common Configuration Mistakes
Several setup errors can compromise the security these technologies are designed to provide:
Leaking DNS queries outside the VPN tunnel happens when your device continues using your ISP’s DNS servers instead of the VPN’s encrypted DNS. This reveals which websites you’re visiting even though the traffic itself remains encrypted. Always verify DNS leak protection is enabled.
Using regular browsers with Tor instead of the dedicated Tor Browser defeats much of Tor’s protection. Regular browsers leak identifying information through WebRTC, JavaScript, and browser fingerprinting techniques that the hardened Tor Browser blocks by default.
Connecting to Tor first then VPN (VPN over Tor) creates a configuration where your VPN provider can potentially see your final destinations. This setup also reveals VPN usage to websites you visit, which may trigger anti-VPN blocks.
Mismatched trust assumptions occur when users trust a VPN provider with Double VPN but don’t verify the provider’s no-logs policy and jurisdiction. Double VPN concentrates risk in a single company – if you can’t trust that company absolutely, the additional server hop provides limited security benefit.
Performance Optimization Strategies
While multi-hop configurations inherently sacrifice speed for security, several strategies can minimize performance impact and maintain acceptable browsing experiences.
Choosing Optimal Server Locations
Server distance dramatically affects latency and throughput. For Double VPN, select server pairs where both locations remain geographically close to your actual position when possible. A Tokyo-Seoul pairing from Japan offers better performance than a Tokyo-London combination.
When security requirements demand specific jurisdictions (such as routing through privacy-friendly countries like Switzerland or Iceland), prioritize having at least one server close to your location. Connect first to a nearby server, then route through the distant jurisdiction as the second hop.
Tor over VPN performance improves when you connect to VPN servers in countries with well-maintained Tor infrastructure. Connecting your VPN to a server in Germany, Netherlands, or Sweden before accessing Tor often provides faster Tor circuits than connecting through countries with fewer Tor nodes.
Protocol Selection Impact
VPN protocol choice significantly affects speed performance, especially with multi-hop configurations where encryption overhead multiplies. Modern protocols like WireGuard provide substantially better performance than older alternatives.
According to performance optimization research, WireGuard offers lightweight operation with low latency – generally the best default for most users. OpenVPN UDP provides balanced security and compatibility with good performance, while TCP variants sacrifice speed for reliability.
For Double VPN, the protocol choice affects both hops. Some providers allow different protocols at each stage, enabling optimization based on network conditions. Using WireGuard for the first hop often delivers the best results.
Tor over VPN benefits from WireGuard or OpenVPN UDP before entering the Tor network. These faster protocols reduce overhead on the VPN side, though Tor’s own routing limitations remain the primary performance bottleneck.
Hardware and Network Considerations
Encryption processing requires CPU resources. On older computers or mobile devices, the double encryption of Double VPN can strain processors and slow performance beyond the network factors. Devices with hardware encryption acceleration (AES-NI instructions on modern processors) handle encryption overhead much more efficiently.
Your base internet connection speed sets the absolute ceiling for VPN performance. Multi-hop configurations typically require at least 25-50 Mbps of base bandwidth to maintain acceptable speeds for activities like streaming, according to VPN speed testing methodologies.
With slower connections, the percentage-based speed reductions of multi-hop VPNs become more noticeable. A 50% reduction from 100 Mbps to 50 Mbps remains adequate for most uses. The same 50% reduction from 10 Mbps to 5 Mbps creates frustrating experiences.
Split Tunneling Applications
Split tunneling allows you to route only specific applications through your Double VPN or Tor over VPN connection while other traffic uses a standard single-hop VPN or direct connection. This optimization strategy balances security and performance.
Route only your most sensitive applications – secure messaging, email, document uploads, or financial transactions – through the multi-hop configuration. Let bandwidth-intensive applications like video streaming or large file downloads use faster connections.
This approach requires careful consideration of your threat model. Split tunneling reduces overall anonymity by creating correlatable traffic patterns. An adversary monitoring multiple connection points could potentially link your multi-hop traffic with your direct traffic based on timing analysis.
Security Limitations and Vulnerabilities
No privacy technology provides perfect protection. Understanding the limitations and potential vulnerabilities of both Double VPN and Tor over VPN helps you make realistic assessments of the security each provides.
Trust Dependencies
Double VPN concentrates significant trust in your VPN provider. The same company operates both servers in the chain and handles all encryption. If that provider logs your connection data, responds to government data requests, or suffers a security breach, your entire privacy protection collapses.
This contrasts sharply with Tor’s trustless model where no single entity controls multiple nodes in your circuit. Evaluating a VPN provider’s trustworthiness becomes critical when relying on Double VPN. Factors like jurisdiction, logging policies, independent security audits, and transparency reports all matter significantly.
Tor over VPN divides trust differently. You must trust your VPN provider not to log your connection to Tor, but the Tor network itself maintains anonymity through its decentralized architecture. This partially mitigates the risk of VPN provider compromise.
Traffic Analysis Threats
Sophisticated adversaries with vast resources can potentially conduct traffic correlation attacks against both technologies. By monitoring traffic entering and exiting the privacy network, attackers might statistically link connections based on timing, volume, and pattern analysis.
Double VPN offers limited protection against such attacks because both hops occur through the same provider’s infrastructure. An adversary with access to that provider’s network could correlate traffic across both servers.
Tor’s random routing through diverse networks makes these attacks substantially more difficult, though not impossible. Nation-state actors with the ability to monitor large portions of internet traffic might succeed in correlating Tor traffic, particularly for high-volume or long-duration connections.
End-to-End Security Gaps
Both technologies protect data in transit but cannot secure endpoints. If your device is compromised with malware, keyloggers, or spyware, no amount of network-level privacy protection matters. The attacker observes your activities directly on your device before any encryption occurs.
Similarly, neither technology protects against compromised destination servers. If you connect to a malicious website or a legitimate site that has been hacked, your data could be captured after decryption at the destination.
HTTPS provides end-to-end encryption between your browser and websites, working independently of VPN or Tor protection. Always verify HTTPS connections when transmitting sensitive data, especially when using Tor where malicious exit nodes might attempt downgrade attacks.
Timing and Pattern Attacks
Your behavioral patterns can undermine privacy protections even when the encryption remains secure. Logging into personal accounts while using Tor over VPN directly links your anonymized traffic to your real identity.
Consistent connection times create patterns that surveillance systems can identify. If you connect to your Double VPN configuration every weekday at 9 AM from the same location, correlation with your work schedule becomes possible.
Unique traffic signatures from specific applications or websites you visit might be identifiable even through encrypted connections. Video streaming services create distinctive traffic patterns that Deep Packet Inspection systems can recognize even without decrypting content.
Cost and Availability Comparison
Practical access to these technologies involves different cost structures and provider availability. Understanding the financial and logistical requirements helps with implementation planning.
Double VPN Service Availability
Most major VPN providers now include Double VPN functionality in their standard subscription tiers. Premium services typically offer this feature at no additional charge beyond the base VPN subscription.
The number of available Double VPN server combinations varies significantly by provider. Some services provide only a handful of pre-configured pairs, while others offer dozens of combinations across various countries and regions.
A few providers charge premium rates for Double VPN access, positioning it as an advanced security feature. However, the market has largely moved toward including multi-hop functionality in standard packages as customer privacy awareness has increased.
Tor Access Costs
The Tor network itself is completely free. The Tor Project operates as a nonprofit organization, and all Tor software is open-source and available at no charge.
When combining Tor with a VPN (Tor over VPN), you only pay for the VPN subscription. Once you have VPN access, adding Tor usage creates no additional costs beyond the time investment in downloading and configuring the Tor Browser.
This cost structure makes Tor over VPN accessible to users with limited budgets who nonetheless need maximum privacy protection. The performance limitations rather than financial barriers represent the primary obstacle to widespread Tor adoption.
Infrastructure Requirements
Both technologies require stable internet connections and modern computing devices capable of handling encryption overhead. Double VPN and Tor over VPN won’t function reliably on very old computers or slow mobile data connections.
Mobile device support varies by platform. Modern smartphones and tablets can run both technologies, though the battery drain from continuous encryption processing becomes noticeable. Double VPN typically proves more practical on mobile devices than Tor over VPN due to better performance.
Router-level VPN implementations allow protecting all devices on a network simultaneously. Some advanced routers support Double VPN configurations, though this requires technical expertise to configure correctly. Tor over VPN typically requires device-level implementation rather than router configuration.
Making the Choice – Which Technology Fits Your Needs
Selecting between Double VPN and Tor over VPN requires honest assessment of your security requirements, acceptable performance trade-offs, and realistic threat models.
Threat Model Assessment
Start by identifying who you need protection from. Different adversaries possess different capabilities, and your privacy technology should match the actual threats you face.
For protection against commercial surveillance, advertising networks, and data brokers, a standard single-hop VPN provides adequate security. These entities rely on mass data collection rather than targeted monitoring, and basic VPN encryption defeats their tracking methods.
Corporate or industrial competitors conducting economic espionage represent a moderate threat requiring enhanced protection. Double VPN provides appropriate defense against these adversaries who possess greater resources than commercial trackers but less capability than state actors.
Nation-state surveillance agencies with sophisticated monitoring capabilities justify Tor over VPN when your activities could attract their attention. Journalists, activists, or security researchers operating in adversarial environments face this level of threat.
Performance Requirements Analysis
Evaluate your actual bandwidth needs against the speed reductions these technologies create. Video conferencing, 4K streaming, or large file transfers become impractical with Tor over VPN’s 50-80% speed reduction.
Double VPN maintains acceptable performance for most activities with its 30-60% speed reduction. This proves adequate for business communications, standard web browsing, and moderate-bandwidth applications.
Consider your tolerance for latency in interactive applications. Online gaming requires sub-50 millisecond latency that neither technology can reliably provide. Real-time video communications work adequately with Double VPN but struggle with Tor over VPN.
Practical Implementation Considerations
Technical comfort level influences which technology you should adopt. Double VPN requires only clicking an option in your VPN application – no technical knowledge necessary. Tor over VPN requires understanding how to properly configure two separate systems.
Your primary use cases determine optimal configurations. If you need privacy protection for regular daily internet usage, Double VPN delivers better usability. If specific high-risk activities require maximum anonymity, switch to Tor over VPN only for those particular sessions.
Device limitations matter for mobile users. Double VPN drains batteries faster than single-hop VPNs but remains practical for several hours of use. Tor over VPN proves less practical on mobile devices due to severe performance impact and battery drain.
Industry Expert Perspectives on Multi-Hop Security
Security researchers and privacy advocates have documented extensive analysis of how multi-hop VPN technologies perform in real-world threat scenarios.
Research published by cybersecurity firms emphasizes that VPN cascading creates meaningful obstacles for traffic correlation attacks. According to technical documentation, even when one server in a chain is compromised, the additional encryption and routing layers maintain significant protection by preventing adversaries from easily linking your original IP address with your final destination.
Privacy organizations note that multi-hop configurations provide particularly strong defense against Internet Service Provider monitoring. When your ISP cannot observe both endpoints of your communication, their ability to profile your online behavior becomes severely limited.
However, security professionals consistently caution against viewing any single technology as a complete solution. Technical analyses published by research organizations emphasize that combining Tor and VPNs can introduce new attack surfaces if improperly configured, potentially leaving users worse off than using either technology correctly in isolation.
Industry testing demonstrates that properly implemented multi-hop VPNs successfully resist many common attack vectors including DNS leaks, IPv6 leaks, and WebRTC leaks when the VPN provider implements comprehensive leak protection.
Cryptography experts highlight that the double encryption in multi-hop VPNs provides genuine redundancy benefits. Government encryption standards maintained by federal agencies confirm that modern encryption algorithms like AES-256 remain secure against current and foreseeable computing capabilities, meaning the redundant layers create robust protection.
Future Developments in Privacy Technology
The landscape of privacy-enhancing technologies continues evolving as both threats and protective capabilities advance. Several emerging trends will likely reshape how multi-hop VPN technologies function.
Post-Quantum Cryptography Integration
Quantum computing threatens to eventually break current public-key cryptography used in VPN protocols. According to CISA’s post-quantum guidance, federal agencies are developing roadmaps for transitioning to post-quantum cryptographic standards.
VPN providers have begun implementing quantum-resistant encryption algorithms. The first providers to deploy these standards in Double VPN configurations will offer protection against future quantum computing capabilities that could threaten current encryption methods.
The transition to post-quantum cryptography may initially increase processing overhead and further impact speeds. However, as dedicated hardware acceleration for these algorithms becomes available, performance should recover to current levels.
Decentralized VPN Networks
Emerging decentralized VPN protocols aim to combine the centralized reliability of traditional VPNs with Tor-like trustless architecture. These systems distribute VPN infrastructure across many independent operators rather than concentrating control in single companies.
Decentralized multi-hop VPNs could potentially offer security approaching Tor’s anonymity with performance exceeding current Double VPN speeds. However, these technologies remain experimental, and their real-world security properties require extensive testing before deployment in high-risk scenarios.
Early implementations face challenges with node reliability, payment mechanisms, and ensuring malicious operators cannot corrupt the network. Solutions to these problems will determine whether decentralized VPNs become viable alternatives to current technologies.
Protocol Optimizations
Ongoing research into VPN protocol design focuses on reducing encryption overhead while maintaining security. Next-generation protocols building on WireGuard’s efficient architecture aim to further reduce latency and processing requirements.
Hardware acceleration for encryption operations continues improving. Modern processors include dedicated instructions for cryptographic operations that can process multi-hop encryption with minimal performance impact compared to software-based encryption.
Machine learning algorithms may optimize routing decisions in multi-hop configurations by predicting network congestion and automatically selecting the fastest available server pairs. This could reduce the current performance penalties while maintaining security benefits.
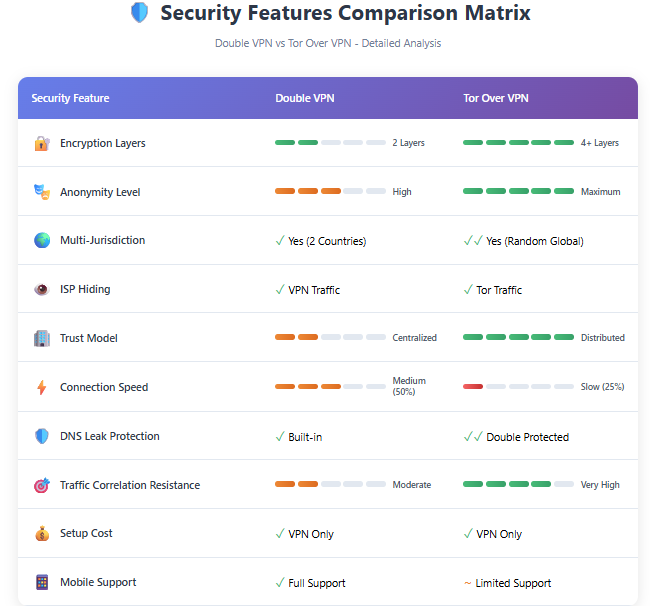
Comparison Table – Double VPN vs Tor Over VPN
| Feature | Double VPN | Tor Over VPN |
|---|---|---|
| Speed Impact | 30-60% reduction | 50-80% reduction |
| Encryption Layers | 2 layers | 4+ layers (VPN + Tor) |
| Anonymity Level | Enhanced | Maximum |
| Setup Difficulty | Very Easy | Easy |
| Trust Model | Centralized (VPN provider) | Distributed (Tor network) |
| ISP Visibility | Sees VPN connection | Sees Tor connection |
| Use Case | Enhanced security with usability | Maximum anonymity |
| Streaming Capability | Adequate | Poor |
| Cost | VPN subscription | VPN subscription |
| Mobile Friendly | Yes | Limited |
Source: Based on technical documentation and performance testing (2024-2025)
Conclusion
Double VPN and Tor over VPN serve different security requirements with distinct trade-offs between privacy protection and usability. Double VPN delivers enhanced security through redundant encryption and multi-jurisdiction routing while maintaining acceptable performance for daily activities, making it ideal for business users and moderate security needs. Tor over VPN provides maximum anonymity through decentralized routing but sacrifices substantial speed, reserving it for high-risk scenarios where exposure creates genuine danger.
Your choice should align with realistic threat assessment rather than pursuing maximum protection regardless of practical impact. Most users benefit from standard single-hop VPNs for routine privacy, switching to multi-hop configurations only when specific activities warrant the performance penalties. As privacy technologies continue evolving with post-quantum encryption and optimized protocols, future implementations may reduce the current speed sacrifices while maintaining strong security.
Understanding these technologies empowers you to implement appropriate protection matching your actual risks without unnecessarily compromising usability. Evaluate your specific needs, test both configurations if possible, and remember that proper implementation matters more than theoretical security capabilities.
Frequently Asked Questions
Q: Can I use Double VPN and Tor together for even more security?
You can technically configure this by connecting to Double VPN and then using Tor Browser, creating a chain with four or more encryption layers. However, this provides diminishing security returns while creating severe performance problems that make most internet activities impractical. For genuine high-risk scenarios requiring maximum anonymity, Tor over VPN (without the Double VPN) already provides protection that even nation-state adversaries struggle to compromise.
Q: Will Double VPN or Tor over VPN protect me if my VPN provider keeps logs?
Double VPN provides no protection if your VPN provider logs connection data, since the same company controls both servers and can correlate your traffic across them. Tor over VPN offers better protection in this scenario – while the VPN provider would know you used Tor, the Tor network itself maintains anonymity so your actual online activities remain hidden. However, selecting a verified no-logs VPN provider remains critical for both configurations.
Q: Why is Tor over VPN so much slower than Double VPN?
Tor’s architecture routes your traffic through at least three volunteer-run servers of varying capacity and geographic distribution, with each hop adding significant latency. These servers often have limited bandwidth and may be located far from each other, creating cumulative delays. Double VPN routes through only two professionally-maintained servers typically optimized for performance, resulting in much faster speeds despite using multi-hop routing.
Q: Which technology better protects against government surveillance?
Tor over VPN provides stronger protection against government surveillance because it uses a decentralized network where no single entity controls your complete traffic path. Double VPN concentrates trust in one company that could be compelled by legal orders to monitor or log your traffic. However, both technologies significantly exceed single-hop VPN protection, and the choice depends on your specific threat model and whether you need the maximum anonymity Tor provides.
Q: Can websites block Double VPN or Tor over VPN connections?
Websites can detect and block both technologies, though Tor faces more severe restrictions. Many streaming services, financial sites, and online platforms block known Tor exit nodes, making Tor over VPN problematic for accessing these services. Double VPN connections appear as regular VPN traffic and typically avoid these blocks, though some sites implement sophisticated VPN detection that may identify multi-hop connections. Neither technology guarantees access to all online services.
Loading newsletter form...