The Hacker’s Handbook: 10 Secrets They Don’t Want You to Know

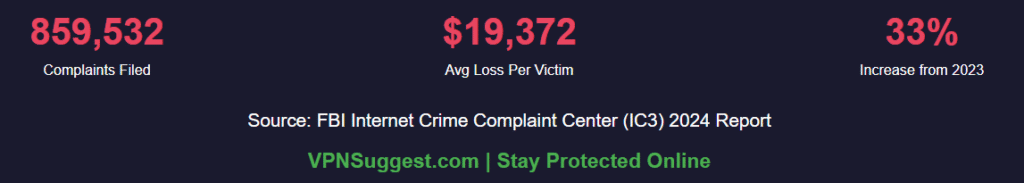
According to the FBI’s 2024 Internet Crime Report, cybercrime losses reached a staggering $16.6 billion – a 33% increase from 2023. With 859,532 complaints filed and hackers stealing an average of $19,372 per incident, understanding how cybercriminals operate isn’t optional anymore. The question isn’t whether you’ll be targeted, but when. By understanding the hacker’s handbook – the exact tactics cybercriminals use daily – you can build defenses that actually work.
Secret #1: Phishing Remains Their Most Profitable Tool
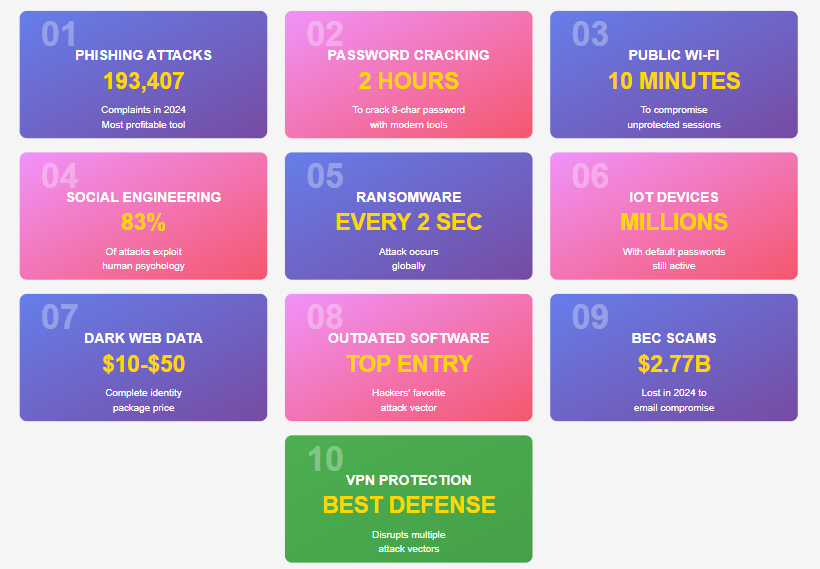
Hackers don’t need sophisticated malware when a simple email works better. Phishing attacks generated 193,407 complaints in 2024 – more than double the next most common cyberattack method, according to FBI IC3 statistics.
How Phishing Actually Works
Cybercriminals create emails that look identical to legitimate messages from banks, government agencies, or popular services. These messages create urgency: “Your account will be suspended,” or “Suspicious activity detected.” The goal is simple – trick you into clicking a malicious link or downloading infected attachments.
Modern phishing campaigns use AI to craft personalized messages. Hackers scrape your social media profiles, learning your employer, interests, and connections. They reference real projects you’re working on and impersonate actual colleagues.
Advanced Phishing Techniques in 2025
Spear phishing targets specific individuals with customized attacks. Instead of sending generic “You’ve won a prize” messages to millions, hackers research high-value targets and craft believable scenarios.
Whaling focuses exclusively on executives and decision-makers. These attacks often impersonate board members or CEOs, requesting urgent wire transfers or sensitive company information.
Smishing (SMS phishing) exploits text messages. People trust texts more than emails, making this method particularly effective. Fake package delivery notifications and two-factor authentication scams dominate this category.
The Electronic Frontier Foundation’s privacy protection research documents how phishing evolves constantly. Cybercriminals adapt faster than most organizations can update their security training.
Real-World Impact
Research from CyberScoop’s analysis of IC3 data shows phishing resulted in $70 million in reported losses during 2024. The actual figure is likely much higher, as many victims never report these crimes.
Industry analysts documented that phishing attacks increased 59% year-over-year, with extortion-based phishing schemes becoming particularly prevalent. These attacks threaten to expose embarrassing information unless victims pay immediately.
Secret #2: Your Password is Easier to Crack Than You Think
Password cracking technology has advanced dramatically. What took hackers months to crack five years ago now takes minutes. Your “strong” password might not be strong enough.
How Hackers Crack Passwords
Brute force attacks systematically try every possible character combination. Modern GPU computing allows hackers to test billions of password combinations per second. An 8-character password using only lowercase letters can be cracked in under two hours.
Dictionary attacks use lists of common passwords and variations. Hackers maintain databases of billions of previously leaked passwords. They test these against new targets because people reuse passwords across multiple sites.
Credential stuffing exploits password reuse. When hackers breach one website, they try those username-password combinations on other platforms. If you use the same password for email, banking, and shopping sites, breaching one gives hackers access to all.
The Mathematics of Password Security
| Password Type | Possible Combinations | Time to Crack |
|---|---|---|
| 8 characters (lowercase) | 208 billion | 2 hours |
| 8 characters (mixed case + numbers) | 218 trillion | 39 days |
| 12 characters (mixed case + numbers + symbols) | 3 quadrillion | 226 years |
| 16 characters (mixed case + numbers + symbols) | 9 septillion | 92 million years |
Source: Based on current computing power estimates (2025)
Why “Password123!” Fails
Adding a number and exclamation point to a dictionary word doesn’t create security. Hackers’ algorithms specifically test these variations. The password “Password123!” appears in every hacker’s common password database.
CISA’s cybersecurity best practices guidance emphasizes that strong passwords must be long, random, and unique. Length matters more than complexity – a 16-character passphrase of random words beats an 8-character string of symbols.
Secret #3: Public Wi-Fi is a Hacker’s Playground
Free Wi-Fi at coffee shops, airports, and hotels creates perfect hunting grounds for hackers. Every device connected to public networks broadcasts data that skilled attackers can intercept.
Man-in-the-Middle Attacks
When you connect to public Wi-Fi, hackers position themselves between your device and the internet. They capture everything you send – passwords, credit card numbers, private messages. You browse normally while they silently record your activity.
Evil twin networks impersonate legitimate Wi-Fi hotspots. A hacker sets up “Starbucks_Guest_WiFi” next to the real Starbucks network. Most people can’t distinguish between them and connect to whichever signal is stronger.
Packet Sniffing Technology
Hackers use freely available software to capture data transmitted over Wi-Fi networks. Without encryption, your browsing history, login credentials, and personal information flow across the network in plain text.
Security researchers documented that unencrypted public Wi-Fi sessions can be compromised in under 10 minutes using basic packet sniffing tools. The attacker doesn’t need sophisticated equipment – a laptop and free software suffice.
The Hotel Wi-Fi Trap
Hotel networks present unique risks. Guests often lower their security guard while traveling, assuming hotels provide safe connections. Hackers specifically target hotel Wi-Fi because travelers frequently access sensitive work information and banking accounts.
Understanding VPN encryption protocols like AES-256 and ChaCha20 becomes critical when using public networks. VPNs create encrypted tunnels that prevent packet sniffing and man-in-the-middle attacks.
Secret #4: Social Engineering Beats Technical Hacking
Why hack a system when you can hack a human? Security experts acknowledge that people remain the weakest link in cybersecurity. Hackers exploit psychology, trust, and authority to bypass even the strongest technical defenses.
The Psychology of Social Engineering
Social engineers manipulate human emotions – fear, curiosity, greed, and helpfulness. They create scenarios where targets feel compelled to act quickly without thinking critically.
Authority exploitation leverages people’s tendency to comply with perceived authority figures. A hacker impersonating IT support can convince employees to disable security software or share credentials.
Urgency creation prevents careful analysis. “Your account will be closed in one hour” or “The CEO needs this wire transfer immediately” pressures victims into making hasty decisions.
Trust abuse exploits established relationships. After researching your social media, hackers impersonate colleagues or friends, making requests seem legitimate.
Real-World Social Engineering Tactics
According to Dark Reading’s analysis of FBI data, social engineering contributed to 83% of successful cyberattacks in 2024. Technical vulnerabilities caused far fewer breaches than human manipulation.
Pretexting involves creating fictional scenarios. A hacker calls your IT department claiming to be a remote employee who forgot their password. They provide enough correct details (gathered through research) to sound legitimate.
Baiting offers something desirable to lure victims. “Free movie downloads” or “Exclusive limited-time offer” tricks people into clicking malicious links or downloading infected files.
Tailgating exploits physical security. Hackers follow employees into secure buildings, counting on people’s politeness to hold doors open. Once inside, they access sensitive systems directly.
The LinkedIn Intelligence Network
Cybersecurity analysts emphasize that professional networking sites provide hackers with valuable intelligence. Your LinkedIn profile reveals your job title, responsibilities, colleagues, and company structure.
Hackers use this information to craft targeted attacks. They know who makes financial decisions, who has system access, and who might be traveling (and therefore distracted). Every post and connection provides attack vectors.
Secret #5: Ransomware Targets Everyone, Not Just Big Companies
The myth that hackers only target large corporations costs small businesses millions annually. Ransomware attacks increased 9% in 2024, with attacks occurring approximately every two seconds, according to FBI Internet Crime data.
How Ransomware Operations Work
Modern ransomware groups operate like legitimate businesses – with customer service departments, pricing tiers, and service level agreements. They maintain professional operations because ransomware generates billions in revenue.
Initial access typically occurs through phishing emails or exploiting unpatched vulnerabilities. Once inside your network, ransomware quietly spreads, mapping your systems and identifying valuable data.
Data encryption happens suddenly. The malware encrypts files across your network, making them inaccessible. Your documents, databases, and backups become locked behind military-grade encryption.
Ransom demands appear with payment instructions. Hackers typically demand cryptocurrency payments, providing a countdown timer to create urgency. Miss the deadline and the ransom doubles – or your data gets permanently deleted.
The Double Extortion Model
Cybercriminals evolved beyond simple encryption. Double extortion involves stealing data before encrypting it. Even if you restore from backups, hackers threaten to publish sensitive information unless you pay.
This tactic proves particularly effective against healthcare providers, law firms, and financial institutions – organizations handling confidential client information. The threat of public disclosure often forces payment regardless of technical recovery capabilities.
Ransomware Statistics That Matter
| Ransomware Metric | 2024 Data |
|---|---|
| Complaints Filed | 3,156 |
| Reported Losses | $12.47 million |
| Average Payment | $200,000 – $2 million |
| Recovery Success Rate | 65% of payers |
| Complete Recovery | Only 8% |
Source: Compiled from FBI IC3 2024 Report
These figures represent only reported incidents. Trustwave’s analysis notes that actual ransomware losses exceed reported figures by an estimated 400%, as many victims never disclose attacks due to reputational concerns.
Top Ransomware Groups in 2025
The most active ransomware variants identified by IC3 include Akira, LockBit, RansomHub, FOG, and PLAY. These groups specifically target critical infrastructure – healthcare facilities, energy companies, and municipal governments.
LockBit operated for years before law enforcement disrupted their operations. However, decentralized ransomware groups quickly filled the void, demonstrating that dismantling one organization doesn’t eliminate the threat.
Secret #6: Your Smart Devices Are Backdoors
Internet of Things (IoT) devices – smart thermostats, security cameras, voice assistants – create thousands of entry points into your network. Most smart devices prioritize convenience over security, making them vulnerable to exploitation.
The IoT Security Problem
Smart devices rarely receive security updates. Manufacturers focus on new products rather than maintaining older devices. A three-year-old smart camera probably contains multiple known vulnerabilities that will never be patched.
Default credentials plague IoT devices. Many ship with usernames like “admin” and passwords like “admin123.” Users rarely change these defaults, allowing hackers to access devices using credential lists available online.
Weak encryption makes intercepting communications easy. Some devices transmit data without encryption at all. Even encrypted devices often use outdated protocols with known vulnerabilities.
How Hackers Exploit Smart Devices
Botnet creation turns IoT devices into attack weapons. Hackers infect thousands of devices, creating networks of compromised systems. These botnets launch massive distributed denial-of-service (DDoS) attacks or mine cryptocurrency using your electricity.
Network pivoting uses one vulnerable device to access others. Once hackers compromise your smart doorbell, they can potentially reach your computer, phone, and any other connected device.
Surveillance leverages smart cameras and microphones. Security researchers repeatedly demonstrate how easily hackers can access camera feeds and audio recordings from poorly secured smart devices.
Research from Industrial Cyber’s report documents that critical infrastructure attacks often begin with compromised IoT devices. Manufacturing facilities lost millions when hackers accessed industrial controls through unsecured smart sensors.
Securing Your Smart Home
Network segmentation isolates IoT devices from critical systems. Create a separate Wi-Fi network for smart devices, preventing them from accessing your main computers and phones.
Regular updates when available reduce vulnerability. Enable automatic updates and periodically check manufacturer websites for firmware patches.
Strong authentication replaces default credentials. Change every device’s password to something unique and complex. Consider whether devices actually need internet access – many work fine on local networks only.
Secret #7: They Buy Your Data on the Dark Web
Your personal information likely exists on dark web marketplaces right now. Data from breaches, leaks, and legitimate sources gets compiled, packaged, and sold to cybercriminals worldwide.
What’s For Sale on Dark Web Markets
Complete identity packages include your name, address, Social Security number, date of birth, and mother’s maiden name – everything needed for identity theft. These packages sell for $10-$50 depending on the victim’s credit score and financial status.
Credit card details with CVV codes cost $5-$30 per card. Hackers buy cards in bulk, testing them on small purchases before making larger fraudulent transactions.
Login credentials for email, social media, and banking accounts sell individually or in massive databases. Collections of millions of username-password combinations cost only a few hundred dollars.
Medical records command premium prices, selling for $50-$1,000 each. Healthcare data contains billing information, insurance details, and personal identifiers that enable sophisticated fraud schemes.
How Your Data Gets There
Data breaches at companies expose customer information. Major retailers, healthcare providers, and even government agencies have suffered breaches compromising millions of records.
According to TRM Labs’ analysis of crypto crime, cryptocurrency remains the payment method of choice for dark web transactions. Bitcoin and privacy coins enable anonymous purchases that traditional payment methods can’t match.
Data brokers legally collect and sell information about your shopping habits, browsing history, and demographics. While legal, this data often ends up accessible through less legitimate channels.
Phishing and malware directly harvests credentials and personal information. Once collected, hackers sell or trade this data on underground markets.
The Data Lifecycle
Your stolen data doesn’t disappear after one use. It gets resold multiple times, combined with new information from subsequent breaches, and packaged into increasingly comprehensive profiles.
Data enrichment combines information from multiple sources. Hackers cross-reference email addresses, phone numbers, and usernames across breaches to build complete dossiers.
Fresh data commands higher prices. Recently stolen credentials work better because victims haven’t changed passwords yet. Older data still has value for long-term identity theft schemes.
Secret #8: Outdated Software is Their Best Friend
Software vulnerabilities provide hackers with ready-made attack paths. When developers discover security flaws, they release patches. Unpatched systems remain vulnerable indefinitely, giving hackers easy targets.
The Patch Management Problem
Organizations struggle to maintain current software across all systems. Testing patches for compatibility takes time. Some legacy systems can’t be updated without breaking critical business functions.
Hackers exploit this reality. They know which vulnerabilities exist in older software versions and actively scan the internet for unpatched systems.
Zero-Day vs Known Vulnerabilities
Zero-day exploits target vulnerabilities unknown to developers. These command premium prices on hacker forums because no defense exists yet. Nation-state actors and sophisticated cybercriminal groups primarily use zero-days.
Known vulnerabilities affect far more victims. After developers release patches, hackers reverse-engineer them to understand the vulnerability. They then target systems that haven’t installed updates.
CISA’s Emergency Directive 25-02 addressing Microsoft Exchange vulnerabilities demonstrates this pattern. Months after patches became available, thousands of organizations remained vulnerable because they delayed updating.
High-Risk Outdated Software
Operating systems running end-of-life versions lack security support. Windows 7, which Microsoft stopped supporting in 2020, still runs on millions of computers. Each one provides an easy target.
Web browsers without current updates expose users to drive-by downloads and malicious websites. Browser vulnerabilities enable hackers to infect systems just by visiting compromised sites.
Plugins and extensions for content management systems frequently contain exploitable flaws. WordPress installations using outdated plugins suffer breaches regularly.
The Update Imperative
Security researchers emphasize that automatic updates provide the best protection. While some organizations need testing periods, individuals should enable automatic updates for operating systems, browsers, and applications.
Critical updates addressing actively exploited vulnerabilities require immediate attention. When Microsoft, Apple, or other major vendors release emergency patches, the situation is urgent.
End-of-life planning prevents using unsupported software. Before operating systems or applications lose support, plan migration to supported alternatives.
Secret #9: Business Email Compromise Steals Billions
Business Email Compromise (BEC) scams generated $2.77 billion in losses during 2024, making it one of cybercrime’s most profitable tactics, according to CertifID’s breakdown of FBI data.
How BEC Attacks Work
BEC scams don’t use malware or technical exploits. Instead, hackers impersonate executives, vendors, or business partners to trick employees into transferring money or sensitive information.
Email spoofing makes messages appear to come from legitimate addresses. Hackers register domains that look nearly identical to real company domains – replacing lowercase “l” with uppercase “I” or adding extra letters.
Account compromise involves gaining actual access to executive email accounts. Once inside, hackers monitor communications to understand business operations, then strike when large transactions are pending.
Social engineering researches targets thoroughly. Hackers identify who handles wire transfers, understand approval processes, and time requests when executives are traveling or unavailable.
Common BEC Scenarios
CEO fraud impersonates the CEO or CFO requesting urgent wire transfers. The email creates time pressure: “I’m in a meeting with acquisition lawyers – we need to wire $500,000 immediately for the deal to close.”
Vendor invoice fraud hijacks legitimate vendor relationships. Hackers monitor conversations about pending payments, then send fake invoices with changed bank account numbers.
Attorney impersonation exploits trust in legal counsel. Fake emails from “law firms” request confidential information or claim settlement funds need to be wired immediately.
Payroll diversion tricks HR departments into changing employee direct deposit information. Hackers impersonate employees, requesting that paychecks be sent to new accounts under their control.
Why BEC Succeeds
BEC attacks succeed because they exploit trust and business processes rather than technical vulnerabilities. No antivirus software detects a legitimate-looking email from what appears to be your CEO.
Industry reports documented that the average BEC attack costs $130,000 per incident. Large-scale attacks targeting international wire transfers can exceed $1 million.
Recovery rates remain low. Once funds transfer, especially internationally or to cryptocurrency exchanges, recovery becomes nearly impossible. The FBI’s Recovery Asset Team freezes less than 70% of reported fraudulent transfers.
BEC Prevention Strategies
Verification protocols require confirming unusual requests through separate communication channels. If your CEO emails requesting a wire transfer, call them to verify using a known phone number – not one provided in the suspicious email.
Multi-approval processes prevent single individuals from authorizing large transfers. Requiring two or three approvals makes BEC attacks significantly harder.
Payment verification checks bank account changes through established channels. When vendors request updated payment information, call them using contact details from previous correspondence, not what’s in the new email.
Secret #10: VPNs Are Their Biggest Obstacle
While hackers have numerous tools, techniques, and exploits at their disposal, VPNs create significant obstacles to their operations. Virtual Private Networks encrypt internet traffic and mask IP addresses, disrupting multiple attack vectors simultaneously.
How VPNs Disrupt Hacker Operations
Traffic encryption renders packet sniffing useless. When you connect through a VPN, your internet traffic travels through an encrypted tunnel. Hackers intercepting this traffic see only encrypted gibberish they can’t decode.
IP address masking prevents targeted attacks. Hackers can’t launch attacks against addresses they don’t know. VPNs replace your real IP address with the VPN server’s IP, making you invisible to network-based attacks.
Public Wi-Fi protection eliminates man-in-the-middle attack opportunities. Even on completely compromised networks, VPN encryption prevents hackers from intercepting your communications.
The VPN Advantage Against Specific Threats
Against phishing attacks, VPNs provide additional protection through secure DNS services. Many VPN providers block known malicious websites, preventing access even if you click phishing links.
For password security, VPNs prevent credential theft during transmission. While they don’t replace strong passwords, they ensure hackers can’t intercept credentials as you enter them on websites.
Against surveillance and tracking, VPNs make establishing accurate user profiles much more difficult. Advertisers, data brokers, and cybercriminals all struggle to track users effectively when VPN connections constantly change IP addresses and locations.
VPN Limitations to Understand
VPNs aren’t magic security solutions. They don’t protect against malware already on your device, can’t prevent social engineering attacks, and won’t stop you from falling for phishing scams.
VPN providers matter significantly. Free VPNs often log your activity, sell your data, or contain malware themselves. Reputable paid VPN services maintain strict no-logs policies and undergo independent security audits.
Choosing Effective VPN Protection
CISA’s cybersecurity awareness guidance emphasizes that strong encryption standards separate effective VPNs from ineffective ones. Look for services using AES-256 encryption or ChaCha20 protocols.
Kill switch functionality prevents data leaks if VPN connections drop. Without this feature, your real IP address and unencrypted traffic could briefly expose to threats during connection interruptions.
No-logs policies verified by independent audits provide genuine privacy protection. VPN providers claiming not to log user activity should prove this through third-party audits.
How to Defend Against These Hacker Tactics
Understanding hacker methods is the first step. Implementation requires concrete defensive measures that address each vulnerability.
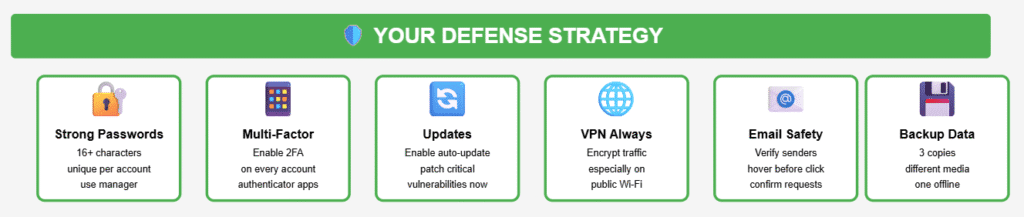
Comprehensive Security Checklist
Enable Multi-Factor Authentication (MFA)
- Add to every account that supports it – email, banking, social media, work accounts
- Use authenticator apps rather than SMS-based codes when possible
- Keep backup codes in secure physical locations
Implement Strong Password Practices
- Use a password manager to generate and store unique passwords
- Create passwords at least 16 characters long
- Never reuse passwords across different services
- Change passwords immediately after any suspected compromise
Maintain Software Updates
- Enable automatic updates for operating systems
- Update applications, browsers, and plugins regularly
- Replace end-of-life software with supported alternatives
- Apply critical security patches immediately
Use VPN Protection
- Connect to VPNs before accessing public Wi-Fi networks
- Choose reputable VPN providers with verified no-logs policies
- Enable automatic VPN connection on startup
- Verify VPN connections before transmitting sensitive information
Practice Email Security
- Verify sender addresses carefully, checking for slight misspellings
- Hover over links before clicking to see actual destinations
- Don’t download attachments from unexpected emails
- Contact senders through known channels to verify unusual requests
Secure IoT Devices
- Change all default passwords immediately
- Create separate networks for smart devices
- Disable features you don’t use
- Research security reputations before purchasing new devices
Backup Critical Data
- Maintain three copies of important data
- Store backups on different media types
- Keep one backup completely offline
- Test restoration procedures regularly
Monitor Accounts and Credit
- Review bank and credit card statements weekly
- Set up transaction alerts for unusual activity
- Check credit reports quarterly
- Consider credit freezes to prevent unauthorized account openings
Organizational Security Measures
Businesses face additional responsibilities beyond individual protections.
Security awareness training should occur quarterly minimum, covering current threats and new attack techniques. Employees represent your frontline defense.
Incident response planning details exactly what to do when breaches occur. Define roles, establish communication protocols, and maintain updated contact lists for security vendors and law enforcement.
Access control policies limit data exposure by implementing least-privilege principles. Employees should only access information necessary for their specific roles.
Network monitoring detects anomalous activity indicating potential compromises. Log analysis can identify attacks in progress before they cause significant damage.
Emergency Response Actions
If you suspect compromise:
- Disconnect from networks immediately to prevent further data exfiltration
- Document everything including times, suspicious activities, and any received communications
- Change passwords for affected accounts from clean devices
- Contact financial institutions to freeze accounts if financial data was exposed
- Report incidents to IC3.gov and local law enforcement
- Engage cybersecurity professionals for forensic analysis and remediation
The FBI’s recommended cybersecurity practices emphasize that rapid response significantly reduces damage. Every hour counts when addressing active breaches.
Conclusion
The hacker’s handbook reveals that cybercriminals rely on predictable techniques – phishing, weak passwords, unsecured networks, social manipulation, and outdated systems. While threats continue evolving, fundamental security principles remain constant.
Encryption, authentication, awareness, and verification form the foundation of effective defense. VPNs provide crucial protection against network-based attacks. Strong unique passwords prevent credential stuffing. Multi-factor authentication blocks unauthorized access. Regular updates close known vulnerabilities.
Your greatest defense against hackers is knowledge combined with action. Understanding these ten secrets means nothing without implementation. Enable your VPN. Update your passwords. Train your employees. Maintain your systems.
Cybercrime costs reached $16.6 billion in 2024, but you don’t have to become a statistic. Start implementing these defenses today – every security measure you add makes the hacker’s job exponentially harder.
Frequently Asked Questions
Q: How often should I change my passwords?
Change passwords immediately after suspected compromises or data breaches affecting services you use. Otherwise, strong unique passwords don’t require regular changes – the old “change every 90 days” advice actually encouraged weaker passwords. Focus on using different passwords for each service rather than frequently rotating the same passwords.
Q: Can antivirus software alone protect me from hackers?
No. While antivirus software provides important protection against known malware, it can’t prevent phishing attacks, social engineering, or zero-day exploits. Comprehensive security requires multiple layers – antivirus, firewalls, VPNs, secure passwords, and security awareness.
Q: Do hackers really target individuals or just big companies?
Hackers target everyone. While headlines focus on major corporate breaches, 46% of all cyberattacks impact businesses with fewer than 1,000 employees. Individual accounts provide access to banking information, identity theft opportunities, and entry points into larger networks.
Q: How can I tell if my email has been compromised?
Check HaveIBeenPwned.org to see if your email appears in known data breaches. Warning signs include receiving password reset emails you didn’t request, noticing sent messages you didn’t write, or friends reporting spam from your address. Change passwords immediately if you suspect compromise.
Q: Are free VPNs safe to use?
Most free VPNs present serious security and privacy risks. They typically log user activity, sell browsing data to advertisers, inject tracking cookies, or contain malware. Reputable VPN services cost money to operate – if you’re not paying, you’re likely the product being sold.
Q: What’s the difference between phishing and spear phishing?
Phishing sends generic scam emails to millions of people hoping a small percentage fall victim. Spear phishing targets specific individuals with customized attacks using researched personal information. Spear phishing has much higher success rates because messages appear more legitimate and relevant.
Should businesses pay ransomware demands?
Law enforcement and cybersecurity experts strongly discourage paying ransoms. Payment doesn’t guarantee data recovery, funds criminal operations, and makes you a target for future attacks. Only 65% of ransomware victims who pay recover their data, and just 8% achieve complete recovery. Focus on prevention and maintain secure offline backups instead.
Q: How do I protect my business from Business Email Compromise?
Implement multi-approval processes for financial transactions, verify unusual requests through separate communication channels, train employees to recognize CEO fraud tactics, use email authentication protocols (SPF, DKIM, DMARC), and establish procedures for confirming vendor banking information changes outside of email.
Loading newsletter form...