VPN Jurisdiction Comparison – 5 Eyes vs 9 Eyes vs 14 Eyes Countries
According to Pew Research Center’s privacy survey, 71% of U.S. adults express concern about how governments use the data they collect – up from 64% in 2019. When you connect to a VPN, you’re trusting that provider with your entire digital footprint. The critical question is whether VPN jurisdiction truly matters for your privacy, or if it’s just clever marketing.
The answer lies in understanding how international intelligence-sharing alliances operate. VPN companies based in certain countries face legal obligations to collect and share user data with government agencies. This guide examines the 5 Eyes, 9 Eyes, and 14 Eyes surveillance alliances and explains how VPN jurisdiction directly impacts your online privacy.
What Are Intelligence-Sharing Alliances?
Intelligence-sharing alliances are cooperative networks among various countries that facilitate the exchange of surveillance data and security information. These alliances allow member governments to monitor digital communications and bypass domestic privacy laws by sharing intelligence with partner nations.
The UKUSA Agreement Foundation
The foundation for modern surveillance cooperation began with the UKUSA Agreement in 1946. According to Wikipedia’s documentation of the UKUSA Agreement, this multilateral treaty established formal cooperation in signals intelligence between the United States and United Kingdom. The alliance expanded to include Canada in 1948, then Australia and New Zealand in 1956.
The initial objective focused on monitoring the Soviet Union during the Cold War. However, as the political landscape shifted, these alliances expanded their scope dramatically. Today, they collect data from internet traffic, phone calls, emails, and virtually every form of digital communication.
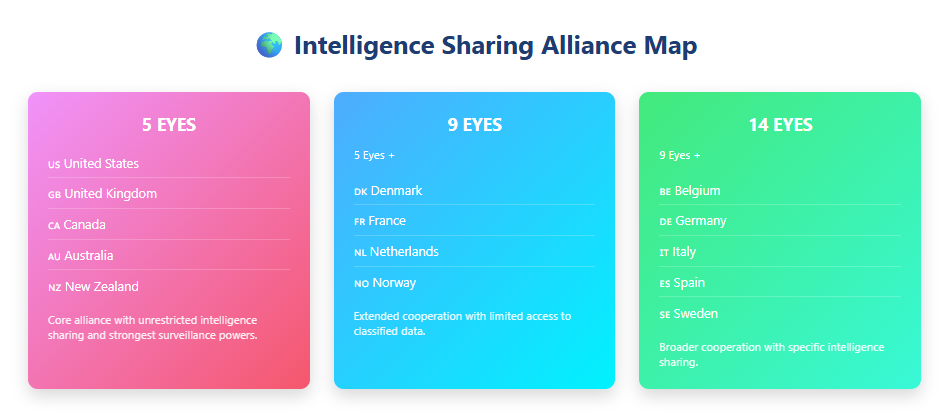
Understanding the 5 Eyes Alliance
The Five Eyes (FVEY) represents the most powerful surveillance network in the world. These five countries maintain unrestricted access to each other’s intelligence databases and coordinate extensive monitoring operations.
Member Countries and Their Surveillance Agencies
United States
- Agency: National Security Agency (NSA)
- Surveillance Law: PATRIOT Act
- Authority: Collect any data deemed necessary for national security, including emails and call records
United Kingdom
- Agency: Government Communications Headquarters (GCHQ)
- Surveillance Law: Investigatory Powers Act
- Authority: Collect internet records and force ISPs to retain user logs
Canada
- Agency: Communications Security Establishment (CSE)
- Surveillance Law: Anti-Terrorism Act
- Authority: Acquire information from global infrastructure for intelligence purposes
Australia
- Agency: Australian Signals Directorate (ASD)
- Surveillance Law: Telecommunications Interception and Access Act
- Authority: Intercept and access stored communications with proper warrant
New Zealand
- Agency: Government Communications Security Bureau (GCSB)
- Surveillance Law: Intelligence and Security Act
- Authority: Intercept communications for national security purposes
How 5 Eyes Countries Bypass Privacy Laws
Research from Comparitech’s guide to intelligence alliances reveals a critical loophole. Each member nation has privacy laws preventing domestic surveillance without warrants. However, 5 Eyes members can spy on each other’s citizens and share the data back.
For example, the NSA cannot legally spy on Americans without a warrant. But GCHQ can monitor Americans and share that intelligence with the NSA. This arrangement effectively circumvents domestic privacy protections across all member countries.
The 9 Eyes Extension – Expanding Surveillance Reach
The Nine Eyes alliance extends Five Eyes cooperation to four additional European nations. These countries share intelligence with the core alliance but receive more limited access to classified data.
Additional Member Countries
- Denmark
- France
- The Netherlands
- Norway
According to CyberNews analysis of surveillance alliances, the Nine Eyes formation brought mainland Europe into the intelligence-sharing framework. While these nations can utilize similar surveillance resources as the 5 Eyes, they don’t automatically access all collected data.
Implications for VPN Users
VPN providers operating in 9 Eyes countries face similar pressures as those in 5 Eyes jurisdictions. Governments can compel these companies to retain user data and provide it to authorities when requested. Even privacy-focused European nations like Denmark and the Netherlands participate in this intelligence exchange.
The 14 Eyes Alliance – SIGINT Seniors Europe
The Fourteen Eyes – officially known as “SIGINT Seniors Europe” or “SSEUR” – represents the broadest intelligence-sharing coalition. Documents leaked by Edward Snowden in 2013 exposed this extended surveillance network.
Complete Member List
The 14 Eyes includes all 9 Eyes members plus:
- Belgium
- Germany
- Italy
- Spain
- Sweden
Surveillance Scope and Data Sharing
Research from VPNMentor’s surveillance analysis indicates that 14 Eyes countries maintain looser cooperation compared to the core alliance. They share specific intelligence but receive limited access to the most sensitive classified information.
However, RestorePrivacy’s detailed investigation notes that data doesn’t stop at 14 Eyes. These countries can sell or share information with additional allies including Israel, Japan, Singapore, and South Korea.
How VPN Jurisdiction Affects Your Privacy
VPN jurisdiction determines which country’s laws govern the provider’s operations. This directly impacts data retention requirements, government access to user information, and the company’s ability to protect customer privacy.
Legal Obligations Under Different Jurisdictions
Countries within surveillance alliances impose varying data retention requirements. According to information from government tracking analysis on vpnsuggest.com, VPN providers must comply with local regulations which may include mandatory data logging, surveillance cooperation, or reporting requirements.
5 Eyes Jurisdictions: Strongest government surveillance powers with extensive legal mechanisms to compel data handover.
9 Eyes Jurisdictions: Similar surveillance capabilities with additional EU privacy regulations providing some protection.
14 Eyes Jurisdictions: Varying levels of government access depending on specific national laws.
Non-Alliance Jurisdictions: Less pressure to cooperate with intelligence-sharing networks, though still subject to local laws.
Data Retention and Access Requirements
The FTC’s enforcement actions against data brokers in 2024 demonstrate how governments actively monitor and regulate data practices. VPN providers face similar scrutiny regarding user information retention and disclosure.
Countries with strict retention laws require VPN companies to store user data for specified periods and provide it to authorities upon request. Privacy-friendly jurisdictions allow providers to maintain stricter no-logs policies without government interference.
Real-World Cases – When VPN Jurisdiction Matters
Several high-profile incidents demonstrate how VPN jurisdiction directly impacts user privacy. These cases reveal the consequences of choosing providers based in surveillance-friendly countries.
IPVanish Data Handover Incident
IPVanish, a U.S.-based VPN provider, handed user logs to federal authorities in 2016. Despite claiming a no-logs policy, the company complied with a government request and provided connection data that led to an arrest. This case highlighted how VPN companies in 5 Eyes countries face significant pressure to cooperate with law enforcement.
PureVPN Malaysia Case
Malaysian VPN provider PureVPN similarly provided user data to U.S. authorities investigating a cyberstalking case. The company shared connection timestamps and IP addresses despite marketing itself as a no-logs service. This incident demonstrated that even providers outside 14 Eyes jurisdictions may cooperate with international law enforcement.
EarthVPN Hong Kong Breach
EarthVPN suffered a data breach that exposed customer information including email addresses, VPN credentials, and plaintext passwords. The incident revealed the provider was logging extensive user data contrary to its privacy claims. Operating from Hong Kong provided no meaningful protection when the company failed to implement proper security practices.
Comparing Privacy-Friendly VPN Jurisdictions
Not all VPN jurisdictions are equal. Some countries maintain strong privacy protections and refuse to participate in international surveillance networks. Understanding these differences helps you select providers that genuinely protect your data.
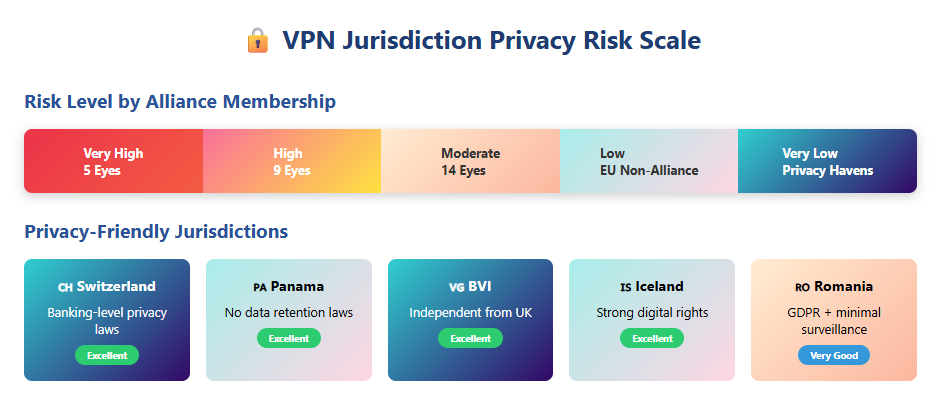
Switzerland – Banking-Level Privacy
Switzerland operates outside all intelligence-sharing alliances. The country’s strict privacy laws and tradition of neutrality make it an ideal VPN jurisdiction. Swiss data protection regulations prevent companies from collecting or sharing user information without explicit consent.
Panama – No Data Retention Laws
Panama has no mandatory data retention requirements and doesn’t participate in intelligence-sharing agreements. The country’s legal framework allows VPN providers to operate truly zero-logs services without government interference. Panama’s privacy laws strongly favor individual rights over surveillance.
British Virgin Islands – Privacy-First Legislation
The British Virgin Islands maintains no data retention laws and operates independently from UK surveillance requirements. Despite the name, this jurisdiction provides strong privacy protections separate from Five Eyes obligations. VPN companies can legally refuse government data requests that violate user privacy.
Iceland – Strong Digital Rights
Iceland enforces comprehensive privacy protections through the Modern Media Initiative. The country’s legal framework strongly protects free speech and digital privacy rights. Iceland doesn’t participate in 14 Eyes intelligence sharing and maintains independent data protection standards.
Romania – EU Privacy Without Surveillance Pressure
Romania offers EU-level privacy protections under GDPR while maintaining minimal participation in intelligence-sharing networks. The country has no mandatory data retention laws and strong constitutional privacy guarantees. Romanian VPN providers operate with fewer surveillance obligations than other EU nations.
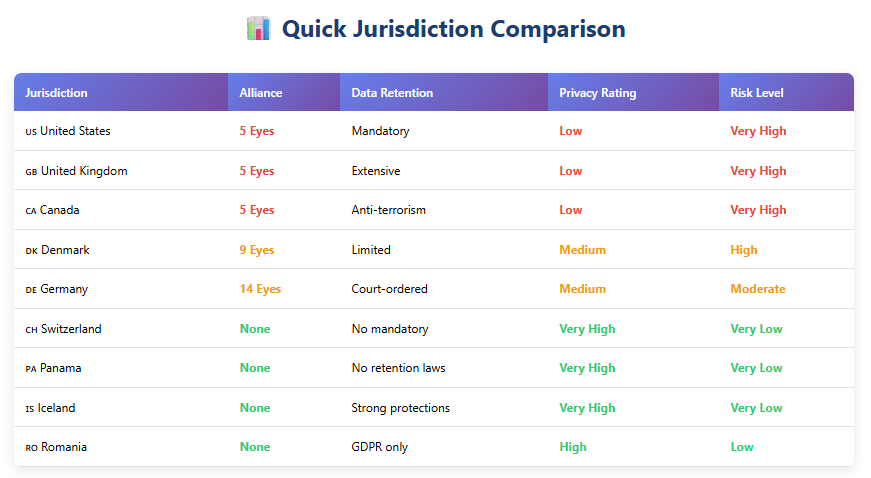
VPN Jurisdiction Comparison Table
| Jurisdiction | Alliance Membership | Data Retention | Privacy Rating | Surveillance Risk |
|---|---|---|---|---|
| United States | 5 Eyes | Mandatory for telecom | Low | Very High |
| United Kingdom | 5 Eyes | Extensive requirements | Low | Very High |
| Canada | 5 Eyes | Anti-terrorism provisions | Low | Very High |
| Australia | 5 Eyes | Warrant-based access | Low | Very High |
| New Zealand | 5 Eyes | Security Act authority | Low | Very High |
| Denmark | 9 Eyes | Limited requirements | Medium | High |
| France | 9 Eyes | Intelligence gathering | Medium | High |
| Netherlands | 9 Eyes | Legal obligations | Medium | High |
| Norway | 9 Eyes | Security provisions | Medium | High |
| Germany | 14 Eyes | Court-ordered access | Medium | Moderate |
| Sweden | 14 Eyes | Intelligence sharing | Medium | Moderate |
| Switzerland | None | No mandatory retention | Very High | Very Low |
| Panama | None | No retention laws | Very High | Very Low |
| Iceland | None | Strong protections | Very High | Very Low |
| Romania | None | GDPR only | High | Low |
Source: Based on international privacy laws and surveillance alliance documentation (2025)
What VPN Providers Won’t Tell You About Jurisdiction
VPN marketing often downplays jurisdiction importance, claiming their no-logs policy eliminates concerns. However, several critical factors reveal why jurisdiction matters regardless of privacy promises.
The No-Logs Policy Limitation
Even legitimate no-logs policies face limitations in surveillance-friendly jurisdictions. Governments can compel VPN companies to start logging specific users through National Security Letters or court orders. Providers may be legally prohibited from disclosing these demands to customers.
Understanding VPN encryption standards matters, but encryption alone cannot protect you if the VPN company must hand over connection metadata to authorities.
Warrant Canaries and Gag Orders
Many VPN providers implement warrant canaries – public statements confirming they haven’t received secret government data requests. When these canaries disappear, it signals the provider may be under legal obligation to cooperate with authorities while remaining silent about it.
5 Eyes countries commonly issue gag orders preventing companies from disclosing surveillance cooperation. VPN providers in these jurisdictions cannot legally warn customers about government data collection even if they wanted to.
Company Ownership and Control
VPN jurisdiction becomes less meaningful if parent companies operate in surveillance-friendly countries. Investigators examining provider ownership often discover shell companies, holding corporations, and complex structures designed to obscure ultimate control.
Always verify the actual corporate structure and ownership chain. A VPN provider “based in Panama” means little if the parent company operates from the United States and controls all infrastructure.
Government Surveillance Programs Revealed by Snowden
Edward Snowden’s 2013 disclosures exposed the massive scope of intelligence alliance surveillance. Understanding these programs helps contextualize why VPN jurisdiction matters for privacy-conscious users.
PRISM – Direct Server Access
PRISM allows NSA direct access to servers of major technology companies including Google, Microsoft, Facebook, and Apple. The program collects emails, video chats, photos, and virtually every form of digital communication. All Five Eyes members access PRISM data.
XKeyscore – Internet Activity Monitoring
XKeyscore tracks internet activity on a global scale. According to Snowden’s revelations, the system lets intelligence agencies read any online communication and determine the location of any internet-connected device. The program processes billions of records daily from internet traffic worldwide.
ECHELON – Global Communications Interception
ECHELON intercepts and analyzes global communications through satellite, telephone, and internet surveillance. The system has operated since the Cold War and continues monitoring international communications. All Five Eyes nations operate ECHELON stations worldwide.
VPN Jurisdiction Red Flags to Avoid
Certain warning signs indicate a VPN provider may not protect your privacy regardless of marketing claims. Watch for these red flags when evaluating VPN jurisdiction and company practices.
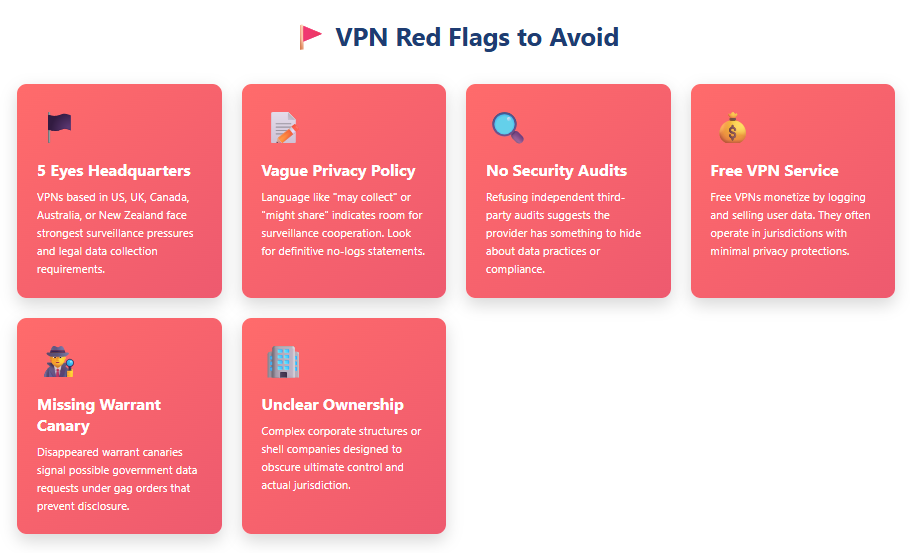
Headquartered in 5 Eyes Countries
VPN providers based in United States, United Kingdom, Canada, Australia, or New Zealand face the strongest government surveillance pressures. These jurisdictions give intelligence agencies extensive legal authority to compel data collection and sharing.
Vague Privacy Policy Language
Privacy policies using ambiguous language about data collection practices signal potential problems. Phrases like “may collect,” “can retain,” or “might share” indicate the provider leaves room for surveillance cooperation. Legitimate no-logs VPNs use clear, definitive language about what they don’t collect.
No Independent Security Audits
VPN providers refusing independent security audits raise serious concerns. Third-party audits verify no-logs claims and confirm companies implement proper security practices. Lack of audits suggests the provider has something to hide about their data practices or jurisdiction compliance.
Free VPN Services
Free VPN providers must monetize somehow. Many generate revenue by logging and selling user data to third parties, advertisers, or data brokers. The FTC has taken multiple enforcement actions against companies misrepresenting their data collection practices.
Free services often operate in jurisdictions with minimal privacy protections, making them particularly vulnerable to government data requests and commercial exploitation of user information.
How to Choose the Right VPN Jurisdiction
Selecting a VPN based on jurisdiction requires balancing multiple factors including threat model, privacy needs, and use case. Follow this framework to make an informed decision.
Assess Your Threat Model
Different users face different privacy risks. Casual users seeking protection from ISP tracking have different needs than journalists working with sensitive sources or activists opposing authoritarian regimes.
Low-Risk Users: Geographic restrictions and basic privacy protection Medium-Risk Users: Protection from government surveillance and data collection High-Risk Users: Protection from state-level actors and sophisticated monitoring
Verify Jurisdiction Claims
Don’t trust VPN marketing about jurisdiction. Independently verify where the company legally operates, maintains servers, and processes user data. Check business registrations, corporate filings, and ownership documentation.
Research the specific privacy laws governing that jurisdiction. Some countries claiming strong privacy protections maintain extensive surveillance cooperation with intelligence alliances through informal agreements.
Examine Infrastructure Location
VPN jurisdiction differs from server locations. A provider based in Switzerland may operate servers in Five Eyes countries. Data passing through those servers potentially faces local surveillance regardless of the company’s home jurisdiction.
Prioritize VPN providers that operate their own infrastructure in privacy-friendly locations. Rented or third-party servers introduce additional risks of data access and monitoring.
Review Independent Audits and Transparency Reports
Legitimate VPN providers undergo regular independent security audits verifying their no-logs claims and privacy practices. These audits should examine:
- Logging practices and data retention
- Infrastructure and server configuration
- Encryption implementation
- Privacy policy accuracy
Transparency reports demonstrating how providers handle government data requests provide additional confidence. Look for providers that publish regular updates about legal demands and their responses.
Privacy Beyond VPN Jurisdiction
While VPN jurisdiction significantly impacts privacy, it represents just one element of comprehensive online security. Implementing multiple privacy layers provides stronger protection than relying solely on VPN location.
Multi-Hop Connections
Multi-hop or double VPN configurations route traffic through multiple servers in different jurisdictions. This approach makes traffic analysis and data correlation significantly more difficult for surveillance agencies. Even if one jurisdiction cooperates with government monitoring, the additional hops provide protection.
Tor Over VPN
Combining Tor network access with VPN connections adds another privacy layer. Your ISP sees only VPN traffic while the VPN provider sees only Tor connections. This configuration prevents either party from viewing both your identity and browsing destination simultaneously.
Encrypted Communications
VPNs encrypt internet traffic but don’t protect message contents after reaching their destination. Use end-to-end encrypted messaging apps, email services, and file sharing platforms regardless of VPN jurisdiction. Tools like Signal, ProtonMail, and encrypted cloud storage provide additional security.
Privacy-Focused Browsers and Extensions
Configure browsers for maximum privacy using extensions that block trackers, fingerprinting, and analytics. Privacy-focused browsers like Brave or hardened Firefox configurations significantly reduce data collection regardless of VPN jurisdiction.
Legal Considerations and Compliance
Understanding legal aspects of VPN jurisdiction helps avoid potential problems while ensuring your privacy practices remain lawful and effective.
VPN Legality by Country
VPN use remains legal in most countries, though some nations heavily restrict or ban virtual private networks. China, Russia, Iran, UAE, and several other countries impose strict regulations on VPN services. Using VPNs in these locations carries legal risks regardless of jurisdiction.
Research local laws before connecting to VPNs while traveling internationally. Some countries consider VPN use for bypassing censorship a criminal offense punishable by fines or imprisonment.
GDPR and EU Privacy Regulations
European Union General Data Protection Regulation establishes comprehensive privacy protections for EU citizens. VPN providers operating in EU jurisdictions must comply with GDPR requirements including:
- Explicit consent for data collection
- Right to access collected information
- Right to deletion of personal data
- Mandatory breach notifications
However, GDPR compliance doesn’t prevent intelligence sharing under 9 Eyes or 14 Eyes arrangements. EU privacy laws apply to commercial data collection but may not restrict government surveillance cooperation.
International Data Transfer Regulations
VPN providers transferring data across international borders must comply with various regulations. The invalidation of Privacy Shield and ongoing challenges to Standard Contractual Clauses impact how VPN companies legally handle user information.
Choose providers that clearly explain their data transfer practices and comply with international privacy frameworks. Transparency about jurisdictional data handling indicates respect for privacy regulations.
Future of VPN Jurisdiction and Surveillance
The landscape of digital surveillance and VPN jurisdiction continues evolving. Several trends will impact privacy protections in coming years.
Expanding Intelligence Alliances
Japan has expressed interest in joining Five Eyes as a potential “Sixth Eye” member. According to RestorePrivacy’s alliance documentation, both United States and United Kingdom have shown interest in expanding core alliance membership.
Additional countries forming intelligence-sharing partnerships will reduce the number of truly privacy-friendly VPN jurisdictions. Users should monitor alliance expansions and adjust VPN selections accordingly.
Encryption Backdoor Demands
Governments increasingly demand encryption backdoors allowing law enforcement access to secure communications. Five Eyes nations regularly pressure technology companies to implement “lawful access” mechanisms. These backdoors fundamentally undermine encryption security regardless of VPN jurisdiction.
The ongoing debate between privacy advocates and law enforcement will shape future VPN capabilities. Strong opposition to backdoors remains essential for maintaining meaningful privacy protections.
AI and Automated Surveillance
Artificial intelligence and machine learning dramatically expand surveillance capabilities. Automated systems can process vast quantities of intercepted communications, identify patterns, and correlate data across multiple sources.
Advanced surveillance technology makes VPN jurisdiction increasingly important. Providers operating outside intelligence alliance influence face fewer pressures to integrate automated monitoring systems or provide bulk data access.
Conclusion
VPN jurisdiction directly impacts your digital privacy in ways that marketing materials rarely acknowledge. Intelligence-sharing alliances like 5 Eyes, 9 Eyes, and 14 Eyes give governments extensive surveillance capabilities that can override even the strongest no-logs policies.
Understanding these surveillance networks empowers you to make informed decisions about VPN selection. Prioritize providers operating in jurisdictions outside intelligence alliances with verified no-logs policies and independent security audits.
Privacy-friendly jurisdictions like Switzerland, Panama, British Virgin Islands, Iceland, and Romania offer the strongest protections against government surveillance cooperation. Combined with proper security practices, these locations provide meaningful privacy in an increasingly surveilled digital world.
Your VPN choice represents just one component of comprehensive privacy protection. Implement multiple security layers, use encrypted communications, and stay informed about evolving surveillance capabilities. The effort you invest in selecting the right VPN jurisdiction pays dividends in long-term privacy protection.
Frequently Asked Questions
Q: Does VPN jurisdiction really matter if they have a no-logs policy?
Yes, jurisdiction matters significantly. Governments in surveillance-friendly countries can compel VPN providers to start logging specific users through secret court orders. Even legitimate no-logs policies cannot protect against mandatory data retention demands backed by legal authority and gag orders.
Q: Are VPNs based in EU countries safe because of GDPR?
GDPR provides important privacy protections for commercial data collection, but it doesn’t prevent government surveillance cooperation. Many EU countries participate in 9 Eyes or 14 Eyes intelligence sharing. For maximum privacy, choose jurisdictions outside all surveillance alliances.
Q: Can I use a VPN server in a privacy-friendly country if my provider is based elsewhere?
Server location and company jurisdiction both matter. Even if you connect to a Swiss server, a VPN provider based in the United States must comply with U.S. surveillance laws. Choose providers with both privacy-friendly jurisdiction and infrastructure.
Q: What’s the single best VPN jurisdiction for privacy?
No single “best” jurisdiction exists. Switzerland, Panama, British Virgin Islands, and Iceland all offer strong privacy protections. The optimal choice depends on your specific threat model, required features, and acceptable trade-offs between privacy and convenience.
Q: How do I verify a VPN provider’s actual jurisdiction?
Research business registrations, corporate filings, and ownership documentation through official government databases. Check who owns the parent company and where they operate. Independent privacy audits and transparency reports provide additional verification of jurisdiction claims.
Loading newsletter form...






