VPN Kill Switch Failure Analysis – When Protection Fails

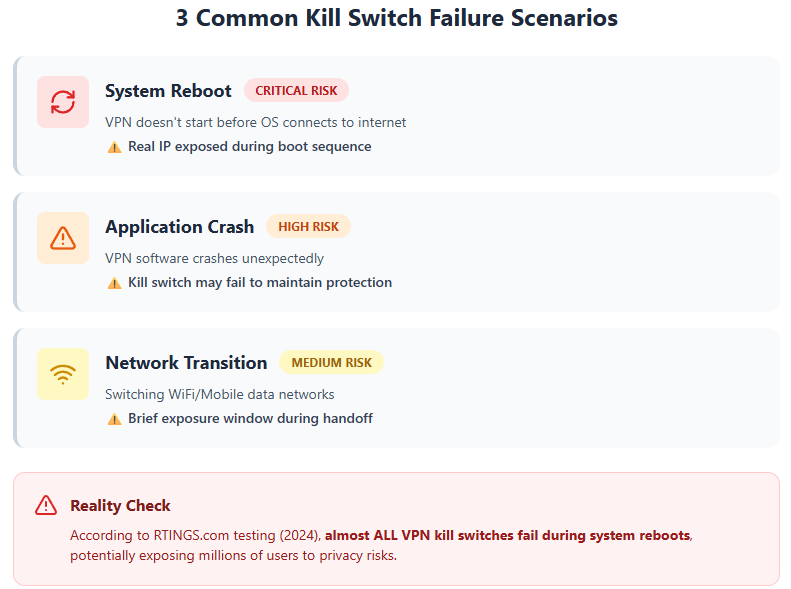
According to comprehensive testing by RTINGS.com in 2024, almost all VPN kill switches fail during a system reboot, potentially exposing millions of users to privacy risks they believe they’re protected against. When you trust a VPN kill switch to safeguard your identity online, understanding exactly when and how these critical security features break down becomes essential for maintaining true privacy.
This analysis examines real-world kill switch failures, the technical reasons behind these breakdowns, and practical strategies to verify your VPN actually protects you when connections drop.
Understanding VPN Kill Switch Mechanics
A VPN kill switch serves as your last line of defense against data exposure. When your encrypted VPN tunnel disconnects unexpectedly, this feature should instantly block all internet traffic until the secure connection restores.
The mechanism continuously monitors your VPN connection status, detecting changes in network conditions or IP addresses. According to security experts, kill switches work through four critical steps – scanning the network, identifying anomalies, blocking connections, and reconnecting once secure.
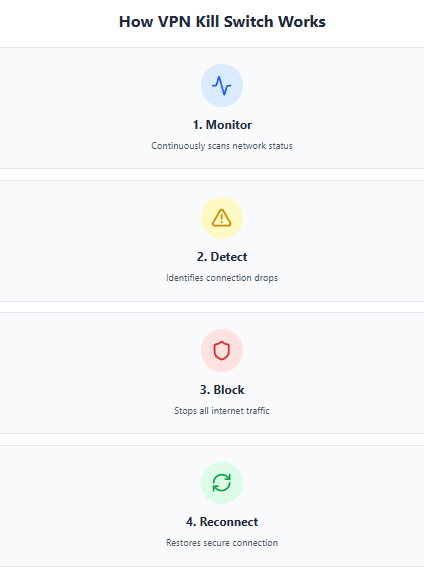
System-Level vs Application-Level Protection
Kill switches operate at two distinct levels. System-level kill switches block all internet traffic when VPN connections fail, ensuring no data escapes your device. This comprehensive approach offers maximum security but disrupts all online activities during disconnections.
Application-level kill switches provide selective protection. You choose which specific apps lose internet access during VPN failures. This flexibility allows critical applications to continue functioning while protecting sensitive activities.
Understanding which type your VPN uses determines your actual exposure during connection failures. Many users assume they have complete protection when their kill switch only guards specific applications.
Common Kill Switch Failure Scenarios
Research from Comparitech’s 2017 study found that most VPNs leak data in certain network disruption scenarios despite having kill switches enabled. These failures occur more frequently than providers acknowledge.
System Reboot Vulnerabilities
The most critical failure point happens during device restarts. Your VPN application may not launch before your operating system establishes internet connectivity. This creates a brief window where traffic flows unencrypted and unprotected.
Testing demonstrates that kill switches frequently fail to prevent internet connectivity immediately after reboots when VPN connections cannot establish properly. Your device connects to networks using your real IP address before VPN protection activates.
VPN Application Crashes
When VPN software crashes unexpectedly, kill switch behavior varies dramatically between providers. Some implementations continue blocking traffic even after the VPN process terminates. Others immediately restore direct internet access.
Process termination tests reveal that certain kill switches partially fail when specific VPN processes are stopped, allowing internet connectivity to fall back to ISP connections. Your protection disappears precisely when you need it most.
Network Transition Failures
Switching between networks creates another vulnerability window. Moving from WiFi to mobile data, connecting to different WiFi networks, or experiencing brief connection interruptions can trigger kill switch gaps.
The time between disconnecting from one VPN server and connecting to another leaves your traffic exposed. This happens during:
- Automatic server switching by VPN clients
- Manual server changes by users
- Network congestion forcing reconnections
- Geographic location changes triggering new server connections
Technical Causes of Kill Switch Failures
The implementation method determines failure rates more than any other factor – kill switches implemented via firewall rules perform differently than those using drivers and system priorities.
Implementation Methods and Weaknesses
VPN providers implement kill switches through various technical approaches. Firewall-based implementations add rules that block non-VPN traffic. These rules can be overridden by system updates, conflicting software, or improper configuration.
Driver-level implementations integrate deeper into your operating system. They intercept network traffic at the kernel level, providing more reliable protection but requiring elevated system permissions.
Poor implementation creates scenarios where kill switches activate too slowly. The delay between connection loss detection and traffic blocking allows data packets to escape through your ISP connection.
Operating System Compatibility Issues
Different operating systems handle network connections uniquely. A kill switch functioning perfectly on Windows may behave unpredictably on macOS or Linux.
VPN connections can drop or fail due to firewall settings, antivirus interference, changes in networks, device issues, server downtimes, VPN crashes, routing problems, and traffic blocks. Each scenario requires specific kill switch responses that implementations frequently miss.
Android and iOS present additional challenges. Mobile operating systems aggressively manage background processes and network connections to preserve battery life. These behaviors can terminate VPN connections without properly activating kill switches.
Timing and Detection Delays
The critical window between connection loss and kill switch activation represents your greatest vulnerability. Kill switches must detect disconnections instantly and block traffic immediately.
Network monitoring occurs at intervals rather than continuously. A 100-millisecond gap between checks allows data packets to leak. During high network activity, dozens of packets containing identifying information can escape.
Real-world testing shows detection delays ranging from milliseconds to several seconds depending on implementation quality and system load. Connection monitoring scans network status in real-time, but the moment network status or IP address unexpectedly changes creates a critical alarm window.
Real-World Data Exposure Risks
When kill switches fail, the information leaking through your ISP connection can severely compromise your privacy and security. Understanding what actually gets exposed helps evaluate the real risks.
IP Address and Location Leakage
Your real IP address becomes immediately visible to any website or service you’re accessing. This reveals your approximate geographic location, ISP identity, and creates a trackable identifier across the web.
Even momentary VPN failures can reveal information VPNs are meant to keep private, including your location, IP address, DNS traffic, IP traffic, and WebRTC traffic. These brief exposures often go unnoticed by users who assume continuous protection.
Third-party trackers, advertisers, and analytics services collect this information instantly. A single exposed connection attempt provides enough data to build profiles linking your VPN-protected and unprotected activities.
DNS Query Exposure
Domain Name System requests reveal every website you visit. When kill switches fail, DNS queries flow through your ISP’s servers rather than your VPN’s encrypted tunnel.
Your ISP now sees complete browsing history. Government agencies or other entities monitoring internet traffic can collect this information. DNS logs persist long after the momentary failure ends.
DNS leaks occur even during brief connection drops because your system immediately attempts to resolve domain names through available DNS servers.
Application Data Leaks
Active applications don’t pause when VPN connections drop. Email clients continue syncing. Messaging apps send and receive messages. File-sharing software maintains connections.
All this activity happens using your real IP address and unencrypted connections. The specific applications running during failure moments determine what data gets exposed.
For professionals handling sensitive information, journalists protecting sources, or activists in restrictive countries, these brief leaks can have severe consequences. Government and law enforcement agencies monitor communications and track online activities through methods including IP address correlation, traffic analysis, and metadata analysis.
Industry Testing and Kill Switch Reliability
Independent testing provides crucial insights into which VPN providers actually deliver reliable kill switch protection. Published research reveals significant variations in performance.
Testing Methodologies
Comprehensive kill switch testing evaluates multiple failure scenarios. Testers simulate network disconnections, application crashes, system reboots, server switches, and network transitions.
Each scenario requires specific testing protocols. System reboot tests verify traffic blocking before VPN connections establish. Network transition tests examine the gap between disconnecting from one server and connecting to another.
Testing methodologies simulate conditions where devices have valid internet connections but VPN fails to establish connections to servers – scenarios where kill switches should block internet access. Proper testing requires technical expertise and controlled network environments.
Provider Performance Variations
Testing results show dramatic differences between VPN providers. Research found that NordVPN and ExpressVPN proved most leak-proof in comprehensive network disruption tests, demonstrating that implementation quality matters more than marketing claims.
Many providers with kill switch features exhibit failures in specific scenarios. Some perform well during application crashes but fail during system reboots. Others handle network transitions effectively but leak data when switching between WiFi and mobile connections.
Users cannot assume kill switch presence guarantees protection. The specific implementation determines actual security during connection failures.
Mobile vs Desktop Reliability
Desktop VPN clients generally provide more reliable kill switch protection than mobile applications. Operating system constraints on iOS and Android limit implementation options.
Many VPN providers offer kill switches in most Windows VPN clients, but some providers may not offer kill switch features for Mac, Android, and iOS devices. This limitation leaves mobile users more vulnerable to data exposure.
Mobile operating systems include built-in VPN kill switch features that can supplement or replace app-specific implementations. Android’s system-level kill switch option provides consistent protection across all VPN applications.
Verification Methods – Testing Your Kill Switch
You cannot trust marketing claims or assume your kill switch works correctly. Active verification through testing confirms whether your VPN actually protects you during connection failures.
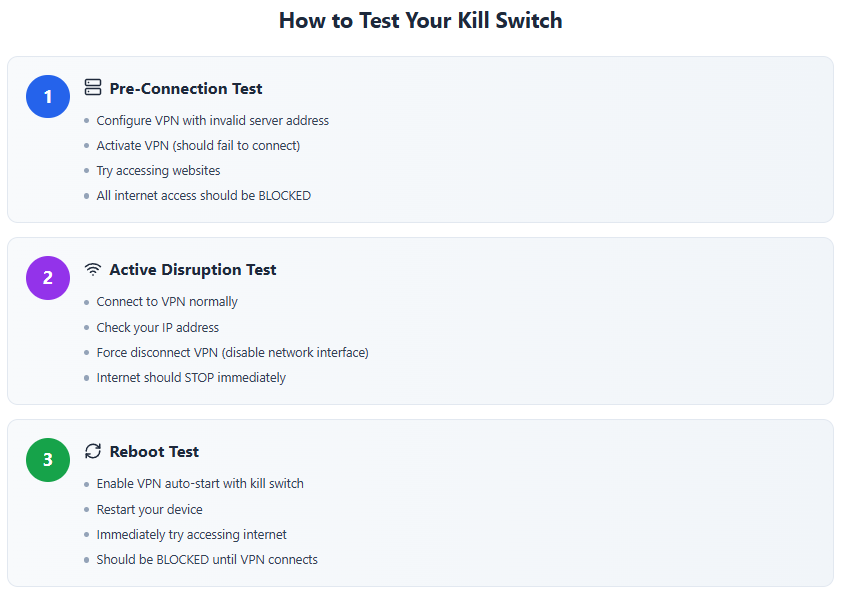
Pre-Connection Testing
Before relying on your VPN for sensitive activities, test kill switch functionality through controlled failures. Configure your VPN with an invalid server address that prevents connection establishment.
Activate your VPN with this invalid configuration. Your kill switch should block all internet access immediately. Test by attempting to access websites, sending emails, or using messaging applications.
When testing scenarios where VPN fails to establish connections, ping tests and connectivity checks should fail completely if kill switches function properly. Any successful internet activity indicates kill switch failure.
Active Connection Disruption Testing
Testing during active VPN connections simulates real-world failure scenarios. Establish a normal VPN connection and monitor your actual IP address through online checking services.
Force connection termination by disabling your VPN’s network interface, blocking VPN traffic through firewall rules, or stopping VPN processes through task managers. Observe whether internet connectivity immediately stops or briefly continues.
Advanced testing monitors network traffic during these disruptions. Tools like Wireshark reveal whether any packets escape through your ISP connection during the transition.
Post-Reboot Verification
System restart testing identifies the most common failure point. Configure your VPN to auto-start on boot with kill switch enabled.
Restart your device and immediately attempt internet access before VPN status becomes visible. Check your IP address, run DNS leak tests, and monitor which applications can access the internet.
Your kill switch should maintain protection from the moment your system boots until your VPN connection fully establishes. Any internet access during this window indicates vulnerability.
Mitigation Strategies and Best Practices
Understanding kill switch limitations enables implementation of additional protection layers. Multiple security measures provide defense-in-depth when individual protections fail.
Layered Security Approaches
Never rely solely on VPN kill switches for privacy protection. Combine multiple security tools to create redundant safeguards against data exposure.
Configure operating system firewalls to block traffic when VPNs disconnect. Create rules allowing internet access only through VPN network interfaces. This provides system-level protection independent of VPN software.
Use VPN-enabled routers to protect all devices on your network. Router-level VPN implementation eliminates per-device kill switch concerns. When the router VPN disconnects, all connected devices lose internet access automatically.
Connection Monitoring and Alerts
Implement active monitoring to detect VPN disconnections immediately. Tools that alert you when IP addresses change or VPN connections drop enable rapid response.
Third-party connection monitoring applications provide notifications when your VPN status changes. These alerts let you stop sensitive activities before significant data exposure occurs.
Regular automated IP address checks verify ongoing VPN protection. Scripts that periodically verify your current IP address matches your VPN server can trigger alerts when discrepancies appear.
Protocol and Configuration Optimization
VPN disconnections occur due to unstable internet connections, software and device problems, server failures, network congestion, and protocol selection. According to security research, using OpenVPN over UDP instead of TCP leads to more unstable connections and frequent drops.
Switch to TCP-based VPN protocols when connection stability matters more than speed. TCP’s error-checking and retransmission mechanisms maintain more reliable connections on unstable networks.
Select VPN servers geographically closer to your location. Distance increases latency and creates more opportunities for connection interruptions. Closer servers provide more stable connections with fewer dropout events.
Configure your VPN to reconnect automatically after disconnections. Enable persistent connection attempts that repeatedly try establishing VPN tunnels until successful. This minimizes unprotected time periods.
Provider Selection Criteria
Choose VPN providers based on demonstrated kill switch reliability rather than marketing claims. Research independent testing results and real-world failure reports.
Verify providers offer kill switches across all platforms you use. Consistent protection requires kill switch availability on Windows, macOS, Linux, iOS, and Android. Understanding how government agencies track VPN users through various methods remains crucial for privacy.
Examine provider privacy policies regarding connection logs and disconnection events. Providers that log connection timestamps, IP addresses, or duration of service create additional exposure risks beyond kill switch failures.
Platform-Specific Considerations
Each operating system presents unique challenges for kill switch implementations. Understanding platform differences helps you protect yourself more effectively.
Windows Kill Switch Implementation
Windows provides the most mature environment for VPN kill switch development. Providers implement robust solutions using Windows Firewall integration, network adapter control, and driver-level traffic management.
Third-party firewall rules supplement built-in kill switches. Create outbound rules blocking all traffic except through VPN adapters. These rules persist independently of VPN software status.
Windows services running at system startup can establish VPN connections before user login. This provides earlier protection during boot sequences compared to user-space applications.
macOS Security Framework Limitations
Apple’s macOS restricts low-level network access more than Windows. VPN applications operate within sandboxed environments with limited system modification capabilities.
macOS Network Extension framework enables VPN kill switch implementations, but with constraints. Applications cannot completely block network access during VPN establishment without specific user permissions.
System Integrity Protection prevents certain network modifications even with administrative privileges. This creates scenarios where kill switches function imperfectly compared to Windows implementations.
Linux Flexibility and Challenges
Linux distributions offer maximum flexibility for kill switch implementation. Direct iptables configuration enables precise network traffic control.
Create iptables rules that default to blocking all traffic while permitting only VPN tunnel traffic. These rules provide reliable system-level kill switch functionality independent of VPN applications.
However, Linux variety creates consistency challenges. Distribution differences, package manager variations, and desktop environment diversity mean kill switch implementations work differently across systems.
Mobile Operating System Constraints
iOS and Android restrict background processes and network control to preserve battery life and system stability. These constraints significantly impact kill switch reliability.
iOS limitations prevent VPN applications from reliably blocking all traffic during connection failures. Apple’s built-in VPN settings provide more consistent kill switch behavior than third-party apps.
Android’s always-on VPN setting with “Block connections without VPN” enabled provides system-level kill switch functionality. This native implementation often outperforms app-specific solutions.
Mobile network transitions between WiFi and cellular connections create particularly challenging scenarios for kill switch implementations. The brief disconnection during handoff frequently bypasses kill switch protections.
Advanced Threat Scenarios
Sophisticated adversaries exploit kill switch failures through targeted attacks. Understanding these scenarios helps evaluate your actual risk exposure.
Targeted Network Disruption
Attackers intentionally disrupting VPN connections force kill switch activations. If kill switches fail, brief data exposure windows reveal identifying information.
Techniques include flooding VPN servers with traffic, exploiting protocol vulnerabilities to force disconnections, or jamming wireless networks to interrupt connectivity.
Government and law enforcement use traffic analysis to detect VPN usage despite encryption. They monitor IP addresses associated with VPN servers, analyze traffic patterns, and examine metadata like connection times and data usage patterns.
Timing Attack Exploitation
Adversaries monitor network traffic for the precise moment between VPN disconnection and kill switch activation. Data captured during these microsecond windows can reveal session information.
WebRTC leaks particularly exploit kill switch failures. Browsers might establish peer-to-peer connections outside VPN tunnels during brief disconnection windows, exposing real IP addresses to remote parties.
DNS prefetching by browsers creates another exploitation vector. Background DNS queries for websites you might visit escape VPN protection during kill switch activation delays.
Geofencing and Tracking Implications
Location services continue operating during VPN disconnections. Your device’s GPS, WiFi positioning, and cellular tower triangulation broadcast your physical location independently of network-level protections.
Applications with location permissions access this data even when kill switches block internet traffic. This information gets transmitted once connectivity restores, revealing locations you visited during VPN downtime.
While VPNs mask IP addresses with VPN server addresses to obscure actual locations, authorities can sometimes correlate IP addresses of VPN servers with user activities through monitoring server logs or network analysis techniques.
Regulatory and Compliance Implications
Kill switch failures create compliance risks for organizations subject to data protection regulations. Understanding these implications helps assess potential liability.
Data Protection Requirements
GDPR, CCPA, and similar privacy regulations require organizations to implement appropriate technical measures protecting personal data. VPN kill switch failures potentially constitute security failures under these frameworks.
When employee devices leak customer data during VPN disconnections, organizations face notification requirements, regulatory investigations, and potential penalties.
According to the FTC’s 2024 data, consumers reported losing more than $12.5 billion to fraud, representing a 25% increase over the prior year. These figures demonstrate the financial impact of security failures.
Breach Notification Triggers
Determining whether kill switch failures constitute reportable breaches requires analysis of what data was exposed, to whom, and for how long.
Brief IP address leaks might not trigger notification requirements. However, extended exposure of browsing history, login credentials, or personal communications likely does.
Organizations should document kill switch testing procedures and failure incident responses. This documentation demonstrates due diligence during regulatory investigations.
Industry-Specific Considerations
Healthcare organizations handling protected health information face stricter requirements. HIPAA mandates encryption for data in transit. Kill switch failures potentially expose ePHI to unauthorized parties.
Financial institutions subject to GLBA safeguards rules must ensure VPN implementations meet security standards. Kill switch reliability factors into overall security posture assessments.
Government contractors handling classified information face the most stringent requirements. VPN kill switch failures exposing classified data trigger serious security investigations and clearance revocations.
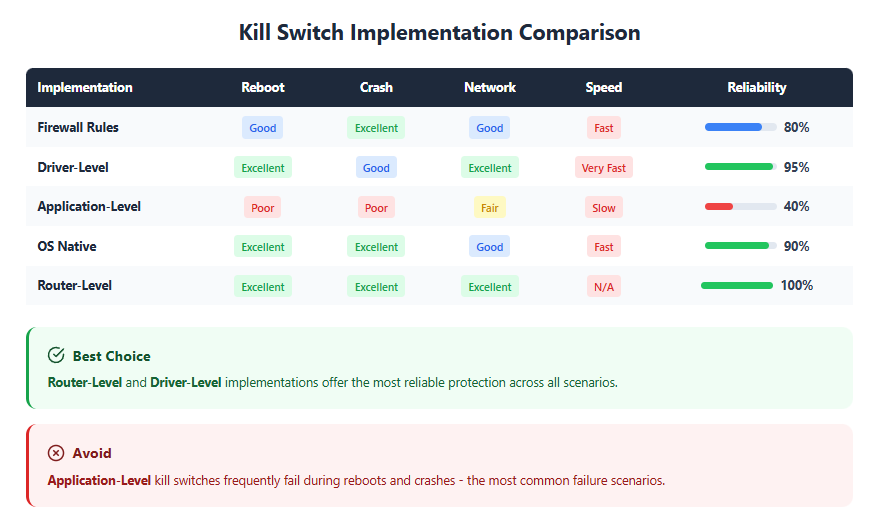
Comparison – Kill Switch Reliability by Implementation Type
| Implementation Method | Reboot Protection | Crash Resistance | Network Transition | Detection Speed | Overall Reliability |
|---|---|---|---|---|---|
| Firewall Rules | Good | Excellent | Good | Fast | High |
| Driver-Level | Excellent | Good | Excellent | Very Fast | Very High |
| Application-Level | Poor | Poor | Fair | Slow | Low |
| OS Native Features | Excellent | Excellent | Good | Fast | High |
| Router-Level | Excellent | Excellent | Excellent | N/A | Very High |
Source: Based on independent security testing and technical analysis (2024)
Emergency Response Procedures
When kill switch failures occur, rapid response minimizes data exposure and security consequences. Establish clear procedures before incidents happen.
Immediate Actions During Failures
Stop all network activity immediately upon detecting VPN disconnections. Disconnect from WiFi networks, disable cellular connections, or power down network adapters.
Do not assume automatic reconnection provides complete protection. Verify your VPN connection fully re-establishes before resuming sensitive activities.
Clear browser caches, cookies, and DNS caches after kill switch failures. This removes tracking identifiers that might have been assigned during unprotected exposure.
Post-Incident Assessment
Document exactly what occurred during the failure. Record the time, duration, applications running, websites accessed, and services contacted.
Check logs from your operating system, VPN client, and firewall to understand traffic that escaped during the failure. Identify what information was potentially exposed.
Review accounts and services accessed during failure windows for unusual activity. Change passwords for services that might have received compromised credentials.
Long-Term Protective Measures
After experiencing kill switch failures, evaluate whether your VPN provider deserves continued trust. Repeated failures indicate implementation problems that may not be fixable.
Consider alternative VPN providers with demonstrated reliability in independent testing. Reputable VPN providers with track records of upholding user privacy protection include those offering strong security features like AES-256 encryption, kill switches, and DNS leak protection.
Implement the additional security layers discussed earlier. Multi-factor protection ensures that single-point failures don’t completely compromise your security posture.
Future of Kill Switch Technology
VPN kill switch technology continues evolving to address current limitations and emerging threats. Understanding development directions helps you make informed decisions.
Hardware-Based Kill Switches
Future implementations may integrate kill switch functionality at the hardware level. Network interface cards with built-in VPN-awareness could block traffic before it reaches software layers.
Hardware kill switches eliminate timing vulnerabilities inherent in software implementations. They provide consistent protection across operating systems and resist software-based attacks or failures.
Protocol-Level Improvements
Next-generation VPN protocols like WireGuard include improved connection stability and faster reconnection capabilities. These characteristics reduce kill switch activation frequency and duration.
Quantum-resistant encryption algorithms under development will require kill switch adaptations. The transition period creates potential vulnerability windows requiring careful management.
AI-Powered Connection Management
Artificial intelligence systems could predict connection failures before they occur. Proactive measures might prevent disconnections rather than just reacting to them.
Machine learning algorithms analyzing network conditions, server load, and environmental factors could trigger preventive actions like server switching before current connections fail.
However, AI implementations introduce new risks. CISA’s 2024 work addressed opportunities and risks AI presents at the intersection of cybersecurity and critical infrastructure, conducting risk assessments that evaluated AI’s potential to increase vulnerabilities.
Expert Insights on Kill Switch Failures
Security researchers have documented critical findings about VPN kill switch reliability through extensive testing and real-world observations.
Network security analysis reveals that kill switch effectiveness varies dramatically based on implementation approach. Research demonstrates that firewall-rule based systems provide more consistent protection than application-level monitoring solutions.
The Verizon 2024 Data Breach Investigations Report analyzed 30,458 real-world security incidents, of which 10,626 were confirmed data breaches spanning 94 countries. This data emphasizes the importance of reliable security implementations across all protection layers.
Cybersecurity specialists emphasize that no kill switch implementation achieves perfect reliability across all scenarios. The key lies in understanding specific failure modes and implementing complementary protections.
According to privacy advocates, strong encryption is tied to one of our most basic rights – the right to have a private conversation, and in the digital world, privacy is impossible without strong encryption.
Conclusion
VPN kill switches provide essential protection against data exposure during connection failures, but comprehensive testing reveals significant reliability gaps across implementations and platforms. The critical window between disconnection and protection activation, combined with scenario-specific failures during reboots, crashes, and network transitions, creates real vulnerabilities that users must understand and mitigate.
Choose VPN providers based on independently verified kill switch performance rather than marketing claims. Implement layered security approaches combining kill switches with firewall rules, connection monitoring, and careful protocol selection. Regularly test your kill switch functionality across different failure scenarios to verify actual protection rather than assumed safety.
The future of online privacy demands more reliable kill switch implementations, but until technology catches up, informed users must take responsibility for verifying their protection actually works when it matters most.
FAQs
Q: How do I know if my VPN kill switch is actually working?
Test your kill switch by intentionally disconnecting your VPN while monitoring your IP address and attempting to access websites. If internet access continues or your real IP address appears during disconnection, your kill switch has failed. Perform tests during system reboots, application crashes, and network switches for comprehensive verification.
Q: Can I trust VPN providers who claim 100% reliable kill switches?
No VPN kill switch achieves perfect reliability across all scenarios. Independent testing consistently shows that even top-rated providers experience failures in specific situations, particularly during system reboots. Verify providers through third-party testing results rather than accepting marketing claims at face value.
Q: What’s the difference between system-level and application-level kill switches?
System-level kill switches block all internet traffic when VPN connections fail, providing comprehensive protection but disrupting all online activities. Application-level kill switches selectively block specific apps you designate, allowing some internet access to continue while protecting chosen applications. System-level provides stronger security but less flexibility.
Q: Do mobile VPN kill switches work as reliably as desktop versions?
Mobile kill switches generally provide less reliable protection than desktop implementations due to operating system constraints. iOS and Android restrict background processes and network control to preserve battery life. Native OS-level kill switch features often outperform app-specific implementations on mobile devices.
Q: What should I do immediately if my VPN kill switch fails and exposes my real IP address?
Stop all network activity immediately by disconnecting WiFi or disabling network adapters. Once reconnected securely, clear browser caches and DNS caches. Change passwords for accounts accessed during exposure. Document what occurred and consider switching to a more reliable VPN provider if failures persist.
Loading newsletter form...
