VPN Protocol Comparison – OpenVPN vs WireGuard vs IKEv2: Which Protocol Wins in 2025?
According to recent industry analysis, the global VPN market reached over 1.6 billion users in 2024, yet most don’t understand the protocols powering their connections. Your VPN protocol determines everything from connection speed to security strength and network stability. The three dominant protocols – OpenVPN, WireGuard, and IKEv2 – each offer distinct advantages, but choosing the wrong one can compromise your online security or significantly slow your connection speeds.
Independent testing reveals that WireGuard outpaces OpenVPN by approximately 57% across various server locations, while IKEv2 excels at maintaining connections during network switches. Understanding these differences is critical for selecting the right protocol for your specific use case, whether that’s streaming, remote work, or mobile browsing.
Understanding VPN Protocols and Why They Matter
A VPN protocol defines how your data travels between your device and the VPN server. Think of it as the instruction manual that governs encryption methods, authentication processes, and connection stability.
These protocols directly impact three critical areas. First, they determine your connection speed through different encryption overhead levels. Second, they control security strength via specific cryptographic algorithms. Third, they affect reliability based on how well they handle network interruptions and transitions.
The protocol you select shapes your entire VPN experience. OpenVPN offers high security, WireGuard provides fast performance, and IKEv2 excels for mobile users, according to recent security assessments.
How Protocol Architecture Affects Performance
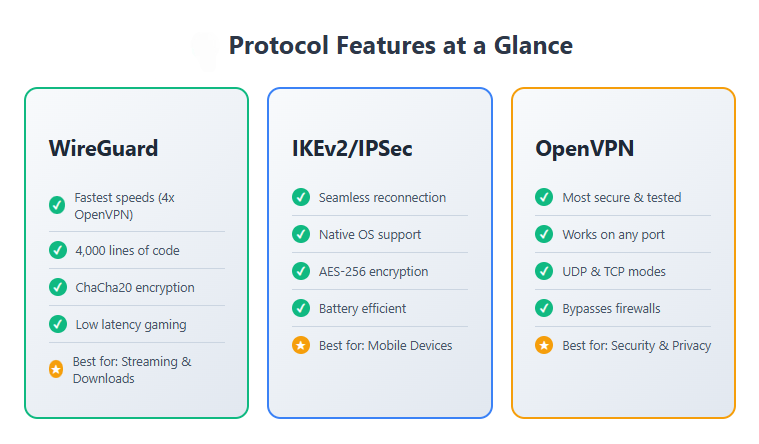
Protocol architecture directly influences real-world performance. WireGuard’s lightweight structure of only 4,000 lines of code makes it less susceptible to security threats compared to protocols with tens of thousands of lines.
This streamlined design enables faster auditing and vulnerability detection. Meanwhile, OpenVPN’s extensive codebase provides remarkable flexibility but introduces additional overhead that can impact connection speeds.
OpenVPN – The Industry Standard Protocol
OpenVPN has dominated the VPN industry since its 2001 release, establishing itself as the benchmark for secure connections. This open-source protocol leverages the OpenSSL library to deliver robust encryption across virtually any platform.
OpenVPN Security and Encryption Standards
The National Institute of Standards and Technology (NIST) recommends IPsec protocols with AES encryption for secure VPN implementations, standards that OpenVPN fully supports through its flexible encryption framework.
OpenVPN typically implements AES-256 encryption, considered unbreakable by current computational standards. The protocol supports multiple cryptographic algorithms including AES, Blowfish, and 3DES, allowing administrators to customize security levels based on specific requirements.
Authentication occurs through certificates rather than pre-shared keys, significantly enhancing security posture. This certificate-based approach prevents unauthorized access even if encryption keys are somehow compromised.
OpenVPN Performance Characteristics
When configured in UDP mode on reliable networks, OpenVPN performs similarly to IKEv2. However, OpenVPN’s larger codebase introduces encryption overhead that can reduce raw speed compared to newer protocols.
The protocol offers both UDP and TCP modes. UDP provides better speed for stable connections, while TCP ensures reliability over unreliable networks. This dual-mode capability makes OpenVPN incredibly versatile across different network conditions.
OpenVPN excels at bypassing restrictive firewalls because it can run on any port using either UDP or TCP. This flexibility proves invaluable in countries with heavy internet censorship or corporate networks with strict security policies.
OpenVPN Platform Compatibility
OpenVPN requires client software installation since no operating system includes native support. However, this actually benefits users by ensuring consistent implementation across platforms.
The protocol works seamlessly across Windows, macOS, Linux, iOS, and Android. Installation typically takes under five minutes, and the configuration process is straightforward for most users.
For enterprise deployments, OpenVPN provides unmatched flexibility in configuration options, logging capabilities, and integration with existing security infrastructure. IT departments can fine-tune every aspect of the VPN connection to meet specific organizational requirements.
WireGuard – The Modern High-Speed Protocol
WireGuard emerged in 2016 as a revolutionary approach to VPN technology, prioritizing simplicity and performance without sacrificing security. This open-source protocol has rapidly gained adoption among major VPN providers and technology companies.
WireGuard Cryptographic Foundation
WireGuard employs ChaCha20Poly1305 encryption for packet encapsulation in UDP, using secure and efficient algorithms that enable fast performance without compromising security.
The protocol utilizes a fixed set of cryptographic algorithms including Curve25519 for key exchange, ChaCha20 for encryption, Poly1305 for authentication, and BLAKE2s for hashing. This curated selection represents the current state-of-the-art in cryptography.
WireGuard implements public key cryptography for establishing connections. Each peer has a public-private key pair, where public keys serve as identifiers. This approach eliminates complex IPsec-style configurations while enhancing security.
WireGuard Speed and Efficiency Advantages
Independent benchmarks consistently demonstrate WireGuard’s performance superiority. The protocol’s minimal overhead and modern cryptographic primitives deliver exceptional throughput on both powerful servers and resource-constrained devices.
WireGuard benchmarks show it achieves almost 4x the speed of OpenVPN in certain configurations. This dramatic performance improvement stems from its streamlined codebase and efficient packet processing.
The protocol maintains low latency during real-time activities, making it ideal for competitive gaming, video conferencing, and live streaming. Every millisecond counts in these applications, and WireGuard’s minimal processing overhead provides measurable advantages.
WireGuard Privacy Considerations
WireGuard was not initially designed with commercial VPN providers offering privacy services in mind, according to privacy-focused VPN providers. The protocol’s default behavior stores user IP addresses on the server for the connection duration.
However, leading VPN providers have developed effective solutions. They implement double NAT systems and dynamic IP assignment to address these concerns while maintaining WireGuard’s performance benefits.
Users should verify how their VPN provider handles VPN privacy policies and what they actually mean before selecting WireGuard. Reputable providers with strict no-logs policies successfully mitigate these inherent privacy challenges.
WireGuard Platform Integration
WireGuard is integrated into the Linux Kernel 5.6, while other operating systems require client app installation. Major platforms including Windows, macOS, Android, and iOS now offer native support.
The protocol’s quick connection times rival or exceed competing protocols. Users typically connect within seconds, and reconnections after network interruptions occur almost instantaneously.
One limitation affects certain networks – WireGuard only supports UDP and cannot fall back to TCP. Network administrators often only allow traffic on ports 80/443 from TCP connections, which can cause issues for WireGuard users on restricted networks.
IKEv2 – The Mobile-Optimized Protocol
IKEv2 (Internet Key Exchange version 2) is part of the IPsec protocol suite, standardized in RFC 7296. Developed as a joint project between Cisco and Microsoft, this protocol has become the preferred choice for mobile users worldwide.
IKEv2 Security Architecture
IKEv2 is paired with IPsec for maximum security, implementing various cryptographic algorithms including AES with 256-bit keys. This combination provides robust protection for sensitive communications.
The protocol supports Perfect Forward Secrecy (PFS) through Diffie-Hellman key exchange. Even if long-term keys are compromised, previous communication sessions remain secure because each session uses unique, ephemeral keys.
IKEv2 employs AES-256-GCM cipher for encryption, SHA2-384 for integrity verification, and 3072-bit Diffie-Hellmann keys. This security stack meets stringent enterprise and government requirements.
IKEv2 Stability and Reconnection Capabilities
IKEv2’s defining feature is its exceptional ability to maintain connections during network transitions. The protocol uses MOBIKE (Mobility and Multihoming Protocol) to seamlessly switch between networks.
IKEv2 offers advantages in terms of speed, security, stability, and the ability to re-establish a connection, making it a solid choice for mobile users. When you switch from Wi-Fi to cellular data, the connection persists without interruption.
This stability proves invaluable for business travelers and remote workers who frequently move between networks. Unlike protocols that drop and reconnect, IKEv2 maintains active sessions even as the underlying network changes.
IKEv2 Performance Profile
IKEv2 is typically faster than OpenVPN due to user-mode encryption, though performance depends on specific connection variables. The protocol delivers high speeds while maintaining strong security.
IKEv2 consumes minimal CPU resources, making it efficient for battery-powered mobile devices. This low resource utilization extends battery life compared to more computationally intensive protocols.
However, IKEv2 faces certain deployment challenges. IKEv2 uses UDP 500 for initial key exchange and UDP 4500 for NAT traversal, making it easier to block than OpenVPN. Restrictive firewalls can prevent IKEv2 connections more easily than OpenVPN alternatives.
IKEv2 Native Platform Support
Most modern operating systems include native IKEv2 support, eliminating the need for third-party software. Windows 7+, macOS 10.11+, iOS, and most mobile operating systems support IKEv2 out of the box.
This native integration enables quick configuration – often taking just minutes to set up. The lack of additional software requirements simplifies deployment in enterprise environments and for non-technical users.
For government tracking concerns and encryption protocols, IKEv2’s strong cryptographic foundation provides reliable protection against surveillance when properly implemented with no-logs policies.
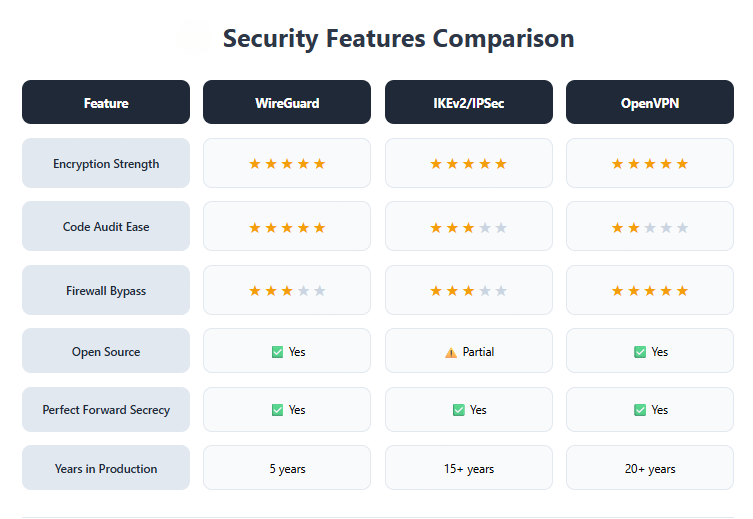
Direct Protocol Comparison – Speed, Security, and Reliability
| Protocol | Average Speed | Codebase Size | Connection Time | Mobile Stability | Firewall Bypass |
|---|---|---|---|---|---|
| OpenVPN | Moderate | ~600,000 lines | 3-5 seconds | Good | Excellent |
| WireGuard | Very Fast | ~4,000 lines | 1-2 seconds | Excellent | Moderate |
| IKEv2 | Fast | ~400,000 lines | 2-3 seconds | Excellent | Moderate |
Source: Based on independent protocol benchmarks and security assessments (2024-2025)
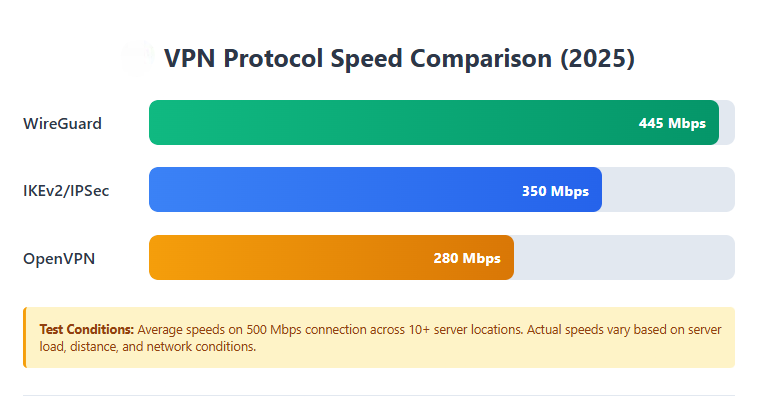
Speed Performance Analysis
Independent tests show WireGuard delivers speeds between 300 Mbps and 445 Mbps on a 500 Mbps connection, significantly outperforming OpenVPN in standardized benchmarks.
WireGuard achieves this performance through its lean codebase and modern cryptography integrated directly into the operating system kernel. The protocol’s streamlined packet processing introduces minimal latency compared to competitors.
IKEv2 typically performs faster than OpenVPN but slower than WireGuard. However, for mobile users, IKEv2’s seamless network switching capability often results in better real-world performance despite slightly lower maximum speeds.
OpenVPN delivers moderate speeds sufficient for most use cases. When configured in UDP mode on stable networks, performance approaches IKEv2 levels. The protocol’s flexibility allows optimization for either speed or maximum security.
Security and Cryptographic Strength
All three protocols provide strong security when properly implemented. NIST-approved algorithms for VPN encryption include AES and Triple Data Encryption Standard (3DES), which these protocols support in various configurations.
OpenVPN offers the most flexibility in cryptographic algorithm selection. Administrators can choose from multiple ciphers, authentication methods, and key exchange mechanisms. This adaptability allows customization for specific threat models.
WireGuard uses a fixed set of carefully selected cryptographic primitives. This opinionated approach reduces configuration complexity and eliminates weak cipher selections. The chosen algorithms represent current best practices in cryptography.
IKEv2 implements robust IPsec security with AES-256 encryption and strong key exchange mechanisms. The protocol’s support for Perfect Forward Secrecy ensures long-term communication privacy even if keys are later compromised.
Reliability Across Network Conditions
Network reliability varies significantly based on connection environment and protocol characteristics.
OpenVPN demonstrates excellent stability over wireless, cellular, and unreliable networks. The protocol includes a TCP mode for highly unreliable connections, though this sacrifices performance due to TCP-over-TCP inefficiency.
WireGuard maintains low ping times due to its streamlined code and minimal overhead, making it a favorite for competitive gaming where every millisecond counts. The protocol handles network roaming better than OpenVPN, maintaining connections while switching between networks.
IKEv2 excels in mobile environments where network conditions change frequently. IKEv2’s built-in stability features ensure smooth performance even when switching between Wi-Fi and cellular connections, making it the top choice for smartphone users.
Platform-Specific Protocol Recommendations
Different devices and use cases demand different protocol selections. Understanding these nuances helps optimize your VPN experience for specific scenarios.
Desktop and Laptop Computers
For Windows and macOS users, all three protocols work well, but the optimal choice depends on your primary activities.
OpenVPN provides maximum flexibility and firewall bypass capabilities. It’s the best choice when working from corporate networks or countries with heavy censorship. The protocol’s ability to run on any port using TCP ensures connectivity in restrictive environments.
WireGuard delivers superior performance for bandwidth-intensive activities. Select this protocol for streaming 4K video, large file downloads, or competitive online gaming. The speed advantages become immediately noticeable with high-bandwidth applications.
IKEv2 offers the quickest setup on systems with native support. If you frequently switch between networks – working from home, cafes, and offices – IKEv2’s seamless reconnection proves invaluable.
Mobile Devices – iOS and Android
Mobile users face unique challenges including battery constraints, frequent network transitions, and varied connection quality.
IKEv2 dominates mobile recommendations due to its exceptional network switching capabilities. IKEv2/IPsec is the best VPN protocol for iPhone and Android users who frequently travel, according to VPN protocol testing across multiple devices.
Native operating system support means faster connections and better battery life. IKEv2 requires no additional software installation on modern smartphones, simplifying configuration for average users.
WireGuard serves as an excellent alternative when maximum speed matters more than connection persistence. The protocol’s low resource usage preserves battery life while delivering impressive throughput.
Router-Based VPN Implementations
Router-level VPN connections protect all devices on your network simultaneously, but protocol selection becomes more limited.
OpenVPN remains the standard choice for router implementations. OpenVPN is supported on DD-WRT with the correct build, and most VPN-capable routers include OpenVPN clients by default.
The protocol’s widespread router support and extensive configuration options make it ideal for whole-home VPN deployments. IT professionals appreciate OpenVPN’s logging capabilities and detailed connection statistics.
WireGuard support is expanding in router firmware, but availability remains inconsistent. Check your specific router model’s capabilities before selecting WireGuard for router-based VPN connections.
Emerging Protocol Developments and Future Trends
The VPN protocol landscape continues evolving as new security threats emerge and performance demands increase.
Post-Quantum Encryption Integration
NordVPN launched post-quantum encryption for the NordLynx protocol in September 2024, complying with the latest National Institute of Standards and Technology (NIST) standards. This development addresses future quantum computing threats.
Post-quantum cryptography prepares for the eventual arrival of quantum computers capable of breaking current encryption standards. The implementation incorporates mathematical algorithms thought to be safe from quantum attacks into VPN infrastructure.
While quantum computers don’t yet pose an immediate threat, forward-thinking VPN providers are implementing quantum-resistant algorithms now. This “harvest now, decrypt later” threat model suggests adversaries could collect encrypted traffic today and decrypt it once quantum computers become available.
Protocol Hybridization Approaches
Major VPN providers are developing proprietary protocols based on established standards. NordLynx builds on WireGuard’s foundation while addressing privacy concerns. ExpressVPN’s Lightway protocol aims for the perfect balance between speed and security.
These hybrid approaches combine proven cryptographic primitives with custom solutions for specific limitations. They represent the industry’s response to evolving user needs and emerging security challenges.
Enhanced Obfuscation Capabilities
WireGuard does not focus on obfuscation, which should happen at a layer above WireGuard according to the protocol’s design philosophy. This has led to development of complementary obfuscation tools.
In regions with VPN blocking, obfuscation technologies disguise VPN traffic as regular HTTPS traffic. While not part of core protocols, these enhancements prove essential for users in restrictive countries.
The Electronic Frontier Foundation recommends checking if VPNs use OpenVPN and WireGuard protocols, which have become common standards for secure connections. These protocols receive ongoing development to enhance privacy and security features.
Choosing the Right Protocol for Your Needs
Protocol selection should align with your specific use case, technical requirements, and security priorities.
For Maximum Security and Privacy
OpenVPN remains the gold standard when security takes absolute priority. Its extensive vetting, open-source transparency, and proven track record make it the most trusted option for sensitive communications.
The protocol’s flexibility allows implementation of the strongest available encryption algorithms. Security-conscious users benefit from OpenVPN’s ability to use certificates for authentication rather than passwords.
Organizations handling confidential information typically standardize on OpenVPN. The protocol’s comprehensive logging and monitoring capabilities enable security teams to detect and investigate potential breaches.
For Speed and Performance
WireGuard dominates when raw performance matters most. WireGuard, Lightway, and NordLynx are the fastest VPN protocols based on current independent testing across multiple scenarios.
Streaming high-resolution video, downloading large files, and competitive gaming all benefit from WireGuard’s exceptional throughput. The protocol introduces minimal latency while maintaining strong security.
Content creators uploading videos, developers pushing large code repositories, and professionals working with high-resolution media files should prioritize WireGuard for its speed advantages.
For Mobile and Travel Use
IKEv2 excels for users constantly on the move. The protocol’s network switching capability prevents dropped connections when transitioning between Wi-Fi networks and cellular data.
Business travelers benefit from IKEv2’s stability when moving through airports, hotels, and conference venues. The seamless reconnection occurs automatically without user intervention.
Battery efficiency represents another mobile advantage. IKEv2’s low CPU usage extends device battery life compared to more computationally intensive protocols.
For Bypassing Censorship and Firewalls
OpenVPN provides superior capability for circumventing restrictions. The protocol’s flexibility to operate on any port using either UDP or TCP makes it difficult to block completely.
In countries with aggressive VPN detection, OpenVPN can be configured to mimic regular HTTPS traffic. This obfuscation capability proves essential for journalists, activists, and users in restrictive regions.
Corporate networks with strict firewall policies often allow OpenVPN traffic when other protocols fail. The ability to run on port 443 using TCP enables OpenVPN to blend with normal web traffic.
Common Protocol Issues and Troubleshooting
Even the best protocols occasionally encounter problems. Understanding common issues helps resolve connectivity problems quickly.
Connection Speed Problems
Slow VPN speeds frustrate users and undermine the VPN experience. Several factors contribute to reduced performance.
Server distance impacts speed regardless of protocol. Connect to geographically closer servers whenever possible to minimize latency and maximize throughput.
Server load significantly affects performance. Oversubscribed servers struggle to maintain high speeds during peak usage times. Switch to less crowded servers to restore performance.
Protocol selection matters tremendously. If OpenVPN feels slow, try switching to WireGuard for the same server. The performance difference can be dramatic, especially on high-speed internet connections.
Frequent Disconnections
Unstable connections disrupt work and entertainment. Different protocols respond differently to network issues.
IKEv2 should maintain connections during network switches. If disconnections occur frequently, verify that MOBIKE is enabled in your VPN client settings. This feature enables seamless network transitions.
OpenVPN in UDP mode may disconnect on unreliable networks. Switch to TCP mode for more stable connections, accepting the performance trade-off for increased reliability.
WireGuard typically maintains stable connections but can struggle with certain NAT configurations. Contact your VPN provider’s support team if WireGuard disconnects persist despite stable internet connectivity.
Firewall and Network Blocking
Some networks actively block VPN protocols through various detection methods.
If IKEv2 won’t connect, the network likely blocks UDP ports 500 and 4500. Switch to OpenVPN on port 443 using TCP to bypass most firewall restrictions.
WireGuard blockages require more creative solutions since the protocol only supports UDP. Some VPN providers offer obfuscation servers specifically designed to bypass VPN detection.
University and corporate networks increasingly implement deep packet inspection to detect and block VPN usage. OpenVPN with additional obfuscation provides the best chance of maintaining connectivity in these restrictive environments.
Expert Recommendations and Best Practices
Industry security analysts and networking professionals offer valuable insights for optimal protocol deployment.
Security Researcher Perspectives
The Electronic Frontier Foundation’s Surveillance Self-Defense guide recommends using services that support well-vetted open source protocols like OpenVPN or IPSec for maximum security assurance.
Open-source protocols benefit from extensive peer review. Thousands of security researchers examine the code, identifying and fixing vulnerabilities before they can be exploited. This transparency builds trust that proprietary alternatives cannot match.
Protocol age and testing history matter significantly. OpenVPN’s 20+ year track record provides confidence that major vulnerabilities have been discovered and patched. WireGuard’s rapid security audits demonstrate the benefits of simpler codebases.
VPN Provider Implementation Quality
Protocol selection represents only part of the security equation. Provider implementation quality critically impacts real-world security and performance.
No-logs policies must be independently verified through audits. Several providers claiming strict privacy practices have been exposed maintaining detailed connection logs. Review recent audit results before trusting any VPN service.
Server infrastructure quality affects both security and performance. Providers operating their own hardware in secure data centers deliver better protection than those relying on virtual servers or third-party hosting.
Kill switch functionality prevents data leaks if the VPN connection drops unexpectedly. This feature proves essential regardless of which protocol you select, providing a critical safety net.
Multi-Protocol Strategy
Advanced users benefit from understanding when to use different protocols rather than committing to a single choice.
Maintain multiple protocol configurations for different scenarios. Use WireGuard for daily browsing and streaming, OpenVPN when connecting from restrictive networks, and IKEv2 on mobile devices.
This flexibility ensures optimal performance and reliability across varying network conditions and security requirements. Modern VPN clients make protocol switching effortless through simple dropdown menus.
Conclusion – Making Your Protocol Choice
Selecting the optimal VPN protocol requires balancing security, speed, and reliability based on your specific requirements. OpenVPN delivers unmatched flexibility and firewall bypass capabilities, making it ideal for users in restrictive environments or those prioritizing maximum security. WireGuard provides exceptional performance with modern cryptography, perfect for bandwidth-intensive activities and users demanding the fastest possible connections. IKEv2 excels for mobile users who need seamless network transitions and efficient battery usage.
The future of VPN protocols looks promising with post-quantum encryption integration, enhanced obfuscation capabilities, and continued performance optimizations. Major providers increasingly offer multiple protocol options, enabling users to select the best tool for each situation rather than committing to a single choice.
Your optimal protocol depends on your primary use case. Evaluate your typical activities, network environments, and security requirements before making a decision. Don’t hesitate to experiment with different protocols – most modern VPN clients make switching effortless, and you may discover that different protocols work better for different scenarios.
Frequently Asked Questions
Q: Which VPN protocol is the most secure in 2025?
All three protocols provide strong security when properly implemented. OpenVPN offers the most mature and extensively audited codebase, making it the traditional choice for maximum security. However, WireGuard’s modern cryptography and minimal attack surface represent cutting-edge security design. Select based on your specific threat model and trust preferences.
Q: Can I use different VPN protocols on different devices?
Absolutely. Most VPN providers support all three protocols across their server networks. You can use WireGuard on your desktop for speed, IKEv2 on your smartphone for stability, and OpenVPN on your router for whole-home protection. Mix and match protocols based on each device’s specific needs and capabilities.
Q: Why is WireGuard so much faster than OpenVPN?
WireGuard’s speed advantage stems from its streamlined codebase and modern cryptographic primitives. The protocol consists of only 4,000 lines of code compared to OpenVPN’s extensive codebase, reducing overhead and enabling more efficient processing. Additionally, WireGuard’s integration into the Linux kernel and use of ChaCha20 encryption provide significant performance benefits.
Q: Will IKEv2 work on all networks?
IKEv2 works excellently on most networks but can face challenges in restrictive environments. The protocol uses specific UDP ports (500 and 4500) that some firewalls block. Corporate networks and countries with VPN blocking may prevent IKEv2 connections. OpenVPN provides better firewall bypass capability when IKEv2 won’t connect.
Q: Should I worry about WireGuard’s IP address logging?
WireGuard’s default design stores IP addresses temporarily, but reputable VPN providers have implemented solutions to address this concern. Look for providers using double NAT systems or dynamic IP assignment with strict no-logs policies. These implementations eliminate privacy concerns while maintaining WireGuard’s performance benefits.
Loading newsletter form...