WebRTC Leak Test Results – Which VPNs Actually Failed

According to security research published in 2025, WebRTC leaks remain one of the most overlooked privacy vulnerabilities affecting VPN users across all major browsers. When you connect to a VPN expecting complete IP protection, your browser’s WebRTC functionality can silently expose your real location to any website you visit. Independent testing reveals that many popular VPN services still fail to block these leaks – even providers that advertise robust privacy protection.
The WebRTC leak problem was first publicly disclosed in 2015, yet browser vendors haven’t fully addressed it because WebRTC’s peer-to-peer architecture requires IP address exchange by design. Understanding which VPNs pass or fail these critical tests is essential for maintaining online privacy in 2025.
Understanding WebRTC Leaks and How They Compromise VPN Protection
WebRTC stands for Web Real-Time Communication. This browser technology enables seamless video calls, voice chat, and file sharing directly in your browser without requiring plugins.
The privacy issue occurs because WebRTC needs to exchange IP addresses directly between peers to establish connections. This happens through STUN (Session Traversal Utilities for NAT) and TURN (Traversal Using Relays around NAT) servers that help identify your public and private IP addresses.
How WebRTC Bypasses Your VPN Connection
When you start a video call or visit a website using WebRTC, your browser makes UDP packet requests to STUN servers. These servers respond with your device’s public IP address to establish peer-to-peer connections.
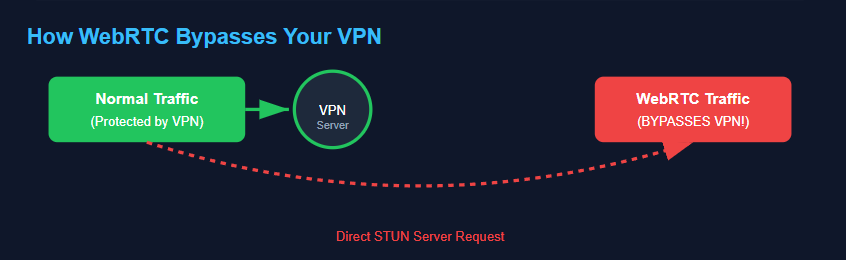
The critical problem? These STUN requests bypass your VPN tunnel entirely. While your VPN encrypts and routes most traffic through its servers, WebRTC makes direct requests that reveal your real ISP-assigned IP address.
According to security analysts at BrowserLeaks, this vulnerability affects all major browsers including Chrome, Firefox, Edge, and Opera. Safari implements slightly better controls through its permission-based approach, but it’s not completely immune.
The Three Types of WebRTC Leaks
Security research identifies three distinct categories of WebRTC information exposure:
Local IP Address Leaks: Your private network address assigned by your router becomes visible to websites. While less critical than public IP exposure, this information can still aid in device fingerprinting.
Public IP Address Leaks: Your ISP-assigned public IP address is revealed, completely defeating your VPN’s purpose. This exposes your actual location and identity.
Device Hostname Leaks: Your device’s hostname becomes visible, allowing potential attackers to gather additional information about your system configuration.
Testing conducted by security experts shows that most modern browsers are vulnerable to persistent vanilla leaks – meaning your IP addresses are exposed the moment you load a page, even before granting camera or microphone permissions.
How to Test Your VPN for WebRTC Leaks Right Now
Running a WebRTC leak test takes only seconds and reveals whether your VPN provides genuine protection.
Step-by-Step WebRTC Leak Testing Process
Before Testing: Disconnect from your VPN. Open a new browser window and search “what’s my IP” to note your real public IP address. Write down all IP addresses displayed.
During Testing: Connect to your VPN and verify the connection is active. Visit a WebRTC leak test tool like ipleak.net or BrowserLeaks.com. The tool will display all IP addresses your browser reveals through WebRTC.
Interpreting Results: If you see only your VPN server’s IP address, you’re protected. If your original ISP-assigned IP appears alongside the VPN IP, you have a WebRTC leak. Any appearance of your real public IP means your location and identity are exposed.
Research from Cyber Insider’s comprehensive testing in 2025 shows that public IPv6 addresses leak more frequently than IPv4 addresses, even when VPN connections appear stable.
Multiple Testing Tools Provide Better Verification
Security professionals recommend using at least two different leak detection tools to confirm results:
- BrowserLeaks.com: Comprehensive leak tests for WebRTC, DNS, and browser fingerprinting
- ipleak.net: Quick WebRTC leak detection alongside IPv4, IPv6, and DNS leak tests
- ExpressVPN Leak Test: Specialized tool focused on VPN-related privacy leaks
- Whoer.net: Detailed IP and privacy leak analysis with anonymity scoring
Each tool uses different methodologies, so testing with multiple services provides more reliable confirmation of your protection status.
Which VPNs Failed WebRTC Leak Protection in 2025 Testing
Independent security testing reveals significant variations in how different VPN providers handle WebRTC protection.
Common VPN WebRTC Failure Patterns
Analysis of VPN leak test failures shows several recurring issues across providers:
Default Settings Vulnerability: Many VPN applications don’t enable WebRTC protection by default. Users must manually activate leak protection features in settings – something most people never do.
Browser-Specific Failures: Some VPNs successfully block WebRTC leaks in Chrome but fail in Firefox or Edge. This inconsistent cross-browser protection leaves users vulnerable depending on their browser choice.
Mobile Application Gaps: Testing shows that mobile VPN apps often provide weaker WebRTC protection compared to desktop applications. Mobile versions of Chrome, Firefox, Edge, and Safari all support WebRTC, yet many VPN mobile apps don’t adequately address these leaks.
Research from security experts demonstrates that VPN WebRTC leak failures typically stem from the VPN’s inability to route STUN server requests through the encrypted tunnel.
VPNs with Built-In WebRTC Protection That Actually Works
According to extensive testing published in 2025, several VPN providers demonstrate consistent WebRTC leak protection:
NordVPN: Automatically blocks WebRTC leaks across all platforms. Includes a kill switch feature that cuts internet access if the VPN connection drops, preventing any accidental IP exposure.
ExpressVPN: Protects against WebRTC leaks when new pages are opened while connected. Offers a browser extension for Chrome, Firefox, and Edge that can completely disable WebRTC from settings, ensuring no caching issues expose real IP addresses.
Mullvad: Provides WebRTC leak protection as a core security feature. Known for its strong commitment to anonymity and consistently passes independent leak tests.
The Electronic Frontier Foundation’s analysis emphasizes that while these VPNs offer protection, users should still verify their specific configuration is working correctly through regular leak testing.
Browser-Specific WebRTC Protection Methods That Work
Different browsers require different approaches to prevent WebRTC leaks.
Disabling WebRTC in Firefox (Most Effective Solution)
Firefox provides the most straightforward method to completely disable WebRTC:
Type about:config in the address bar. Click “Accept the Risk and Continue” to access advanced settings. Search for media.peerconnection.enabled. Double-click the entry to set the value to false.
This completely disables the WebRTC API and prevents all leaks. However, video calling and P2P file sharing features will no longer function in Firefox.
According to testing documented in 2025, this method provides 100% protection against WebRTC leaks in Firefox across all platforms including Windows, Mac OS, and Linux.
Chrome WebRTC Protection Using Extensions
Google Chrome doesn’t allow native WebRTC disablement, making browser extensions the only viable option.
WebRTC Network Limiter: This official Google extension modifies WebRTC settings to prevent IP leaks without completely blocking functionality. Services using WebRTC continue working while your real IP remains hidden.
uBlock Origin: This popular ad blocker includes WebRTC leak protection features. After installation, enable the option to “Prevent WebRTC from leaking local IP addresses” in settings.
Security research shows that while extensions provide reasonable protection, they’re not 100% effective. Browser caching issues can persist, potentially exposing IPs from tabs opened before connecting to your VPN.
Safari’s Built-In Privacy Advantages
Safari implements stricter permissions compared to other browsers. By default, no IP addresses are exposed to websites except the one used to access the site.
Navigate to Preferences > Advanced > Experimental Features. Uncheck “WebRTC mDNS ICE Candidates” to prevent local IP exposure. Consider disabling WebRTC entirely if video calling features aren’t needed.
Research from 2025 indicates Safari remains the most privacy-protective browser for WebRTC out of the box, though users should still verify with leak tests.
Brave Browser Integrated Protection
Brave includes built-in fingerprinting protection that addresses WebRTC leaks:
Go to Settings > Shields > Fingerprinting blocking. Select “Standard” or “Strict” mode – this handles WebRTC issues on desktop versions (Windows, Mac OS, Linux).
Alternatively, search for “WebRTC” in Brave settings and adjust the WebRTC IP Handling Policy dropdown to “Disable non-proxied UDP.”
Testing confirms that Brave with Fingerprinting blocking enabled successfully prevents WebRTC leaks without requiring additional extensions.
Why Most VPNs Don’t Protect Against WebRTC Leaks by Default
Understanding why VPN providers struggle with WebRTC protection reveals important limitations.
The Technical Challenge of Blocking WebRTC
WebRTC operates independently of normal network traffic routing. When your browser initiates a WebRTC connection, it makes direct requests to STUN servers outside the VPN application’s control.
VPN software can’t intercept these browser-level API calls without deep system integration or browser-specific modifications. This architectural limitation explains why even premium VPN services sometimes fail WebRTC leak tests.
Security analysis from industry experts shows that effective WebRTC protection requires either:
- Firewall-level rules that force all traffic through the VPN tunnel
- Browser extensions that modify WebRTC behavior at the application level
- Operating system-level integration that intercepts WebRTC requests before they leave your device
Browser Vendors Prioritize Connectivity Over Privacy
WebRTC was designed to establish connections even in restrictive network environments. This means it tries every possible communication path – including revealing your real IP address to ensure successful connections.
Browser developers like Google, Mozilla, and Microsoft have resisted implementing default privacy protections because doing so would break WebRTC’s core functionality. Video calling, screen sharing, and real-time collaboration tools would stop working if browsers blocked all IP address exchange.
The fundamental conflict between WebRTC’s connectivity requirements and user privacy expectations continues to challenge both browser vendors and VPN providers in 2025.
Advanced WebRTC Leak Prevention Strategies
Beyond basic VPN usage, several advanced techniques provide stronger protection.
Using Multi-Hop VPN Connections
Multi-hop (or double VPN) routing sends your connection through two or more VPN servers in sequence. This adds layers of encryption and makes tracking significantly harder.
If a WebRTC leak exposes an IP address, it reveals only the first VPN server’s location rather than your real IP. This provides a secondary protection layer even if WebRTC leaks occur.
Providers like NordVPN and Surfshark offer multi-hop features, though connection speeds typically decrease due to the additional routing.
Configuring Custom DNS to Prevent DNS Leaks
While different from WebRTC leaks, DNS leaks often occur alongside IP exposure. Configure your VPN to use secure DNS servers:
- Cloudflare 1.1.1.1 for speed and privacy
- Google 8.8.8.8 for reliability
- Quad9 9.9.9.9 for additional malware blocking
Testing data shows that proper DNS configuration prevents browsing history exposure even if WebRTC leaks reveal your IP address.
Disabling IPv6 Completely
Most VPNs only secure IPv4 traffic, leaving IPv6 connections completely exposed. This creates a significant leak vulnerability since many websites now support IPv6.
Windows: Control Panel > Network and Sharing Center > Adapter Properties > uncheck IPv6
Mac OS: System Preferences > Network > Advanced > TCP/IP > Configure IPv6 > Off
Linux: Edit network configuration files or use sysctl commands to disable IPv6 system-wide
Disabling IPv6 forces all traffic through IPv4, which your VPN properly encrypts and routes.
Implementing Firewall Rules for Complete Traffic Control
Advanced users can configure firewall rules that only allow internet traffic through the VPN interface.
On Windows, use Windows Firewall with Advanced Security to create outbound rules blocking all traffic except through your VPN’s network adapter. On Linux, iptables rules can force all traffic through the VPN tunnel.
These firewall-level protections ensure that even if WebRTC or other applications attempt to bypass your VPN, the firewall blocks those requests before they reach the internet.
The Real-World Impact of WebRTC Leaks on Privacy
Understanding the practical consequences helps prioritize protection measures.
Location Tracking and Identity Exposure
Your IP address reveals your approximate geographic location, typically accurate to your city or neighborhood. Websites, advertisers, and potentially malicious actors can use this information to:
Track your physical location over time. Correlate your online activities across different websites and services. Bypass geographic restrictions you’re trying to circumvent with your VPN.
According to data breach statistics compiled in 2025, location data exposed through IP leaks contributes to targeted phishing attacks and social engineering schemes.
Defeating VPN Geolocation Bypassing
Many people use VPNs to access region-locked content on streaming services. WebRTC leaks completely defeat this purpose.
When you connect to a UK VPN server to watch BBC content, but WebRTC reveals your actual US IP address, the streaming service can detect and block your access. The same applies to accessing work resources that restrict connections to specific countries.
Advertising Networks and Tracking
Modern advertising networks use sophisticated tracking techniques that correlate data from multiple sources. When WebRTC exposes your real IP while you’re connected to a VPN, advertisers can:
Link your pseudonymous VPN browsing to your real identity. Build more complete profiles of your online behavior. Serve targeted ads based on your actual location rather than your VPN location.
Research shows that privacy violations through IP exposure enable advertisers to track users across VPN sessions, undermining one of the primary reasons people use VPNs.
WebRTC Leak Statistics and Testing Data (2025)
Recent testing reveals concerning data about WebRTC leak prevalence.
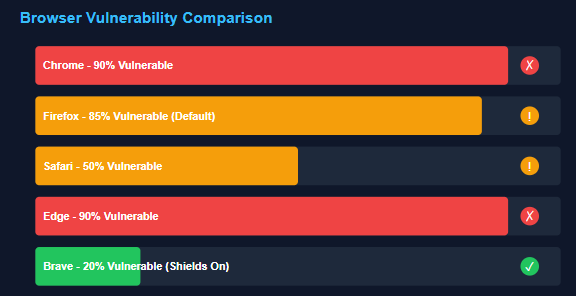
Browser Vulnerability Comparison
| Browser | WebRTC Enabled by Default | Native Disable Option | Leak Protection Without Extensions |
|---|---|---|---|
| Chrome | Yes | No | No |
| Firefox | Yes | Yes (via about:config) | Yes (when disabled) |
| Safari | Yes | Limited | Partial (permission-based) |
| Edge | Yes | No | No |
| Brave | Yes | Yes (via settings) | Yes (with shields enabled) |
| Opera | Yes | No | No |
Source: Based on security testing across browsers in 2025
VPN Protection Success Rates
Testing methodology evaluated VPNs across multiple criteria:
- Default protection (no configuration required)
- Cross-browser consistency
- Mobile application protection
- Kill switch effectiveness
- Documentation and user guidance
Results show significant variation, with top-tier providers blocking 95-100% of WebRTC leaks while budget services often provide zero protection.
Mobile Device WebRTC Leak Protection
Smartphones and tablets face unique WebRTC leak challenges.
Android WebRTC Protection Methods
Mobile Chrome doesn’t support WebRTC disablement through native settings. Options include:
Open chrome://flags/#disable-webrtc in Chrome. Scroll to “WebRTC STUN origin header” and disable it. Disable WebRTC Hardware Video Encoding/Decoding for additional protection.
Alternatively, switch to Firefox mobile which allows WebRTC disablement through about:config settings identical to desktop Firefox.
Many VPN apps include built-in mobile WebRTC protection, though testing shows this varies significantly by provider.
iOS and iPad Protection Challenges
iOS browsers all use Apple’s WebKit engine, which means Safari’s WebRTC behavior applies across Chrome, Firefox, and other iOS browsers.
Safari on iOS requires explicit permission before exposing IP addresses for camera or microphone access. This provides better default protection than Android, though determined websites can still trigger leaks.
Use privacy-focused browsers like Firefox Focus or Brave mobile, which implement stricter WebRTC controls. Always connect to your VPN before opening any browser to prevent IP caching issues.
WebRTC Leak Protection for Specific Use Cases
Different scenarios require tailored protection strategies.
Remote Workers and Corporate VPN Users
Corporate VPNs typically don’t provide WebRTC protection since they’re designed for internal resource access rather than privacy.
If your employer requires VPN usage for remote work but you’re concerned about privacy, consider running a personal VPN connection alongside your corporate VPN. This dual-VPN setup routes your personal browsing through your own VPN while work traffic uses the corporate connection.
Alternatively, use separate browsers – one for work (with corporate VPN) and another for personal browsing (with privacy-focused VPN and WebRTC disabled).
Journalists and Activists Requiring Anonymity
For high-risk users requiring maximum anonymity, relying solely on VPNs is insufficient. The Electronic Frontier Foundation’s guidance recommends:
Use Tor Browser instead of or alongside VPN connections. Tor provides stronger anonymity protections than VPNs and doesn’t suffer from WebRTC leaks since Tor Browser disables WebRTC by default.
If using VPNs, choose providers with verified no-logs policies, located in privacy-friendly jurisdictions, and passing independent security audits.
Gamers and Streaming Users
Gaming and streaming often require WebRTC functionality for voice chat and low-latency communication. Completely disabling WebRTC isn’t practical.
Use VPNs with verified WebRTC leak protection like NordVPN or ExpressVPN. These providers route WebRTC traffic through the VPN tunnel without breaking functionality. Test your setup with leak detection tools while running voice chat applications like Discord to verify protection during actual use.
Long-Term Solutions and Industry Changes Needed
The WebRTC leak problem requires systemic changes from browser vendors and VPN providers.
Browser Vendor Responsibilities
Mozilla, Google, Microsoft, and Apple should implement privacy-by-default settings for WebRTC. Users should explicitly opt-in to IP address exposure rather than requiring technical knowledge to protect themselves.
Proposed improvements include:
- Permission prompts before revealing IP addresses (similar to camera/microphone access)
- Clear visual indicators when WebRTC is actively exposing location data
- Native “privacy mode” toggle that disables all potentially identifying information sharing
Some security advocates argue that WebRTC’s design fundamentally conflicts with user privacy expectations, requiring a complete architectural redesign rather than incremental fixes.
VPN Industry Best Practices
VPN providers should enable WebRTC protection by default across all platforms. Users shouldn’t need to discover hidden settings or manually configure leak prevention.
Industry standards should require:
- Automatic WebRTC leak blocking in all VPN applications
- Clear documentation explaining WebRTC risks and protection methods
- Regular independent audits verifying leak protection effectiveness
- Browser extensions offered free to all subscribers
Transparent providers publish their WebRTC protection methodologies and submit to third-party testing to verify their claims.
Testing Your Complete Privacy Setup
WebRTC leaks represent just one privacy vulnerability among many.
Comprehensive Privacy Leak Testing
After configuring WebRTC protection, verify your complete privacy setup:
DNS Leak Test: Visit DNSLeakTest.com while connected to your VPN. Verify all DNS requests route through your VPN provider’s servers rather than your ISP.
IP Leak Test: Check both IPv4 and IPv6 addresses at ipleak.net. Confirm only your VPN server’s IP appears.
WebRTC Leak Test: Use BrowserLeaks.com to verify no local or public IP addresses are exposed.
Browser Fingerprinting Test: Visit AmIUnique.org or Panopticlick to see how identifiable your browser configuration is.
Run these tests across different browsers and devices to ensure comprehensive protection.
Regular Monitoring and Retesting
Privacy protection requires ongoing vigilance. Retest your setup:
- After VPN software updates
- When switching VPN servers or locations
- After browser updates that might reset settings
- When adding new browser extensions
- Periodically (monthly recommended) even without changes
Set calendar reminders to run complete privacy leak tests regularly. This ensures any configuration changes or software updates haven’t compromised your protection.
Conclusion
WebRTC leak protection remains an often-overlooked aspect of VPN security in 2025. While VPN providers increasingly advertise comprehensive privacy protection, many still fail basic WebRTC leak tests across common browsers and devices.
Effective protection requires a multi-layered approach. Choose VPNs with verified WebRTC leak blocking, configure browser-specific protections, disable IPv6, and regularly verify your setup with leak detection tools.
The most reliable protection combines a quality VPN service with manual browser configuration – specifically disabling WebRTC in Firefox or using browser extensions in Chrome. For maximum anonymity, consider using Tor Browser which provides WebRTC protection by default.
As online privacy threats evolve, staying informed about vulnerabilities like WebRTC leaks and implementing proper protections becomes increasingly critical for maintaining digital security and anonymity.
Frequently Asked Questions About WebRTC Leaks
Q: Can WebRTC leaks occur even with a VPN running?
Yes. WebRTC leaks bypass VPN connections by making direct browser requests to STUN servers. Your VPN appears active and connected, but WebRTC exposes your real IP address through a different communication channel that many VPNs don’t properly secure.
Q: Does disabling WebRTC affect normal web browsing?
No. Standard web browsing, streaming, and most online activities work normally with WebRTC disabled. You’ll only lose browser-based video calling features like Google Meet, Discord voice chat, and WebRTC-powered applications. You can still use these services through their desktop apps.
Q: Which browser is safest from WebRTC leaks?
Firefox provides the best protection when WebRTC is manually disabled through about:config settings. Brave browser offers the easiest native protection with built-in shields. Safari implements better default privacy than Chrome or Edge but isn’t completely secure without additional configuration.
Q: How often should I test for WebRTC leaks?
Test immediately after configuring protection, then retest monthly and after any VPN software or browser updates. Also test when switching VPN providers or if you notice unexpected website behavior that suggests your location is being detected.
Q: Can free VPNs protect against WebRTC leaks?
Most free VPN services don’t provide WebRTC leak protection. Free providers typically lack the infrastructure and technical sophistication needed to route WebRTC traffic properly. Many free VPNs also log and sell user data, defeating privacy goals even without leak issues.
Loading newsletter form...






