Split Tunneling Security Risks Most Users Don’t Know

According to Verizon’s 2024 Data Breach Investigations Report, 68% of breaches involved a human element, with misconfigured security tools contributing significantly to organizational vulnerabilities. Split tunneling – a VPN feature that routes some traffic through an encrypted tunnel while sending other traffic directly to the internet – has become increasingly popular among remote workers seeking better performance.
However, this convenience creates security gaps that most users don’t understand. When you enable split tunneling, you’re essentially creating a backdoor that bypasses critical security protections, potentially exposing sensitive data to cybercriminals and compliance violations.
What Split Tunneling Actually Does to Your Network Security
Split tunneling divides your internet connection into two separate streams. Some traffic flows through your VPN’s encrypted tunnel while other traffic goes directly through your internet service provider.
This configuration might seem practical for bandwidth management. You can access local printers while connected to your corporate VPN or stream Netflix without slowing down work applications.
But here’s what happens beneath the surface – your unencrypted traffic becomes visible to anyone monitoring the connection, including hackers, ISPs, and potentially malicious actors on public networks.
How Split Tunneling Bypasses Corporate Security Measures
Organizations implement multiple layers of defense to protect their networks. Firewalls, intrusion detection systems, and data loss prevention tools all work together to monitor and block threats.
Split tunneling actively circumvents these security measures. When you route traffic outside the VPN tunnel, it bypasses your organization’s security infrastructure entirely.
Your company’s DNS filtering can’t block malicious domains if traffic doesn’t flow through the corporate network. Threat detection systems can’t identify command-and-control communications from malware when that traffic takes the public route.
The Trojan Horse Effect of Compromised Endpoints
A compromised device with split tunneling enabled becomes a bridge into your corporate network. Hackers exploit this vulnerability through a method security professionals call lateral movement.
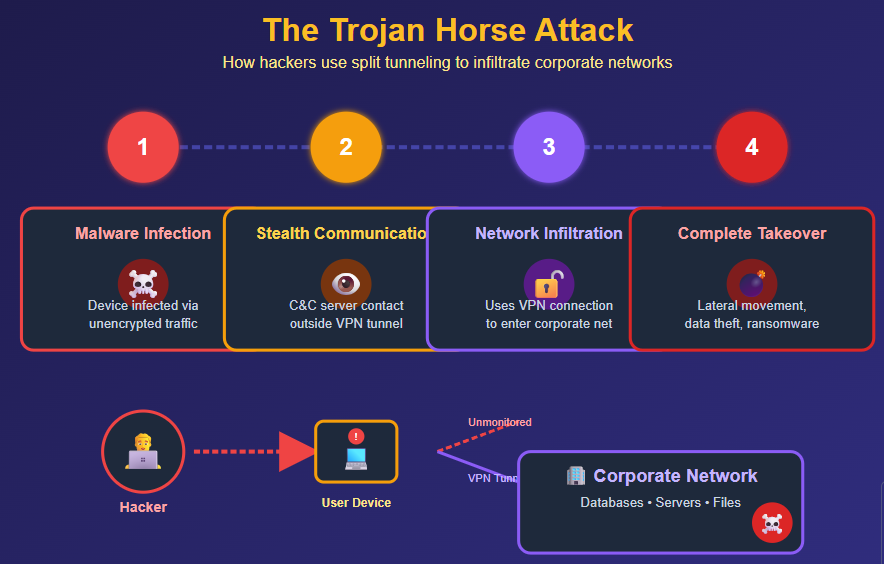
First, malware infects your device through the unencrypted connection. The malware establishes communication with the attacker’s command-and-control server outside the VPN tunnel – completely invisible to corporate security teams.
Once established, the malware uses your VPN connection to infiltrate the corporate network. Security teams have no visibility into the initial infection because that traffic never touched their monitoring systems.
Data Exposure Risks That Catch Users Off Guard
Most users don’t realize how easily they can accidentally expose sensitive information through split tunneling. The risks multiply when you use the same applications for both personal and professional purposes.
Mixed-Use Application Vulnerabilities
Web browsers represent the most dangerous split tunneling risk. You might keep personal social media tabs open alongside work-related cloud applications and corporate resources.
When your browser is exempt from VPN protection through split tunneling, all its traffic – including those work tabs – flows unencrypted through the public internet. Sensitive business data mixes with unencrypted traffic, potentially exposing proprietary information, customer data, or confidential communications.
The problem intensifies with cloud-based collaboration tools. Applications like Slack, Microsoft Teams, or Google Workspace might run outside your VPN tunnel without your knowledge, depending on how split tunneling rules are configured.
DNS Leaks and Privacy Violations
DNS requests reveal which websites you visit, even when the actual content is encrypted. Split tunneling can cause DNS leaks that expose your browsing activity to anyone monitoring the connection.
When your DNS queries bypass the VPN tunnel, they travel unencrypted to your ISP’s DNS servers. This creates a detailed log of your internet activity that can be accessed by your ISP, government agencies, or hackers who compromise those systems.
Privacy threats from DNS leaks can reveal your actual identity and location, defeating the primary purpose of using a VPN in the first place.
Compliance and Regulatory Nightmares
Organizations operating in regulated industries face severe penalties for inadequate data protection. Split tunneling can create compliance violations that result in massive fines and reputational damage.
Healthcare Industry Vulnerabilities
Healthcare organizations must comply with HIPAA regulations that mandate specific security measures for protecting patient health information. HITRUST assessors specifically evaluate split tunneling configurations to ensure they don’t create unauthorized data paths.
When healthcare workers access electronic health records through split-tunneled connections, protected health information may flow outside HIPAA-compliant security controls. Even accidental misrouting of this data constitutes a reportable breach.
According to federal data, consumers reported losing more than $12.5 billion to fraud in 2024, with data breaches playing a significant role in enabling identity theft and financial fraud.
Financial Services and GDPR Requirements
Financial institutions face strict requirements under regulations like GDPR, PCI-DSS, and various banking security standards. These frameworks often mandate that all data transmission occurs through approved, monitored channels.
Split tunneling can violate these requirements by creating unauthorized exceptions to compliance guidelines. Organizations can face substantial fines even when no actual data theft occurs, simply for failing to maintain proper security controls.
The consequences extend beyond fines. Regulatory violations damage customer trust, trigger costly audits, and can result in the loss of certifications required to operate in certain markets.
Remote Work Creates Perfect Storm Conditions
The shift to remote work has dramatically increased split tunneling risks. Home networks lack the security infrastructure of corporate environments, creating additional vulnerabilities.
Unsecured Home Networks Amplify Threats
Most home routers ship with default passwords and outdated firmware. Home networks typically lack enterprise-grade firewalls, intrusion detection systems, or network segmentation.
When employees connect to corporate resources through split-tunneled VPNs from these unsecured networks, they create a direct path from vulnerable home devices into the corporate network.
A hacker who compromises the employee’s home network gains access to the corporate environment through that employee’s VPN connection. The attack succeeds because split tunneling allows the hacker’s traffic to bypass security monitoring.
Public Wi-Fi Magnifies Exposure
Coffee shops, airports, and hotels offer convenient connectivity for remote workers. These public networks are notoriously insecure and frequently targeted by cybercriminals.
Man-in-the-middle attacks on public Wi-Fi can intercept unencrypted traffic from split-tunneled connections. Attackers can capture login credentials, session cookies, and sensitive data that flows outside the VPN tunnel.
The Federal Trade Commission took action against 20 companies between August 2023 and August 2024 for data privacy and security breaches, highlighting the serious consequences of inadequate security measures.
Configuration Complexity Leads to Security Gaps
Implementing split tunneling securely requires careful planning, testing, and ongoing monitoring. Most organizations underestimate this complexity, leading to dangerous misconfigurations.
Common Misconfiguration Mistakes
Application-based split tunneling rules must specify exactly which applications use the VPN tunnel. Companies can accidentally allow unencrypted access to internal databases from external networks through misconfigured rules.
URL-based rules face similar challenges. Websites change their infrastructure, applications update their network behavior, and new cloud services emerge constantly. Rules that worked yesterday may create vulnerabilities today.
Inverse split tunneling – where you specify what stays outside the VPN rather than what goes through it – is particularly error-prone. One missing exclusion can expose critical systems to the public internet.
Platform Inconsistencies Across Devices
Maintaining consistent split tunneling policies across Windows, macOS, iOS, and Android devices presents significant challenges. Each platform handles VPN connections differently.
Organizations often fail to configure mobile devices properly, leaving gaps that enable data leaks. An employee might have secure desktop access but completely unprotected mobile access to the same resources.
Testing split tunneling configurations across all devices, use cases, and data types requires substantial effort. Most organizations lack the resources to perform this comprehensive validation.
Malware Detection Becomes Nearly Impossible
Modern malware is sophisticated and stealthy. It quietly establishes persistence before taking obvious actions. Split tunneling gives malware the perfect cover to operate undetected.
Command-and-Control Communication Hiding
Malware needs to communicate with attacker-controlled servers to receive instructions and exfiltrate stolen data. These command-and-control communications are the primary way security teams detect infections.
When malware routes its traffic through split-tunneled connections, corporate security infrastructure never sees these communications. The malware operates freely while IT teams remain unaware of the compromise.
The malware can also use split tunneling to mask its network behavior. Traffic patterns that would normally trigger alerts blend into regular internet usage when flowing through the public connection.
Delayed Breach Discovery
According to CISA’s cybersecurity guidance, organizations must implement continuous monitoring and rapid threat detection to protect critical infrastructure.
Split tunneling extends the time between initial compromise and discovery. Every extra day attackers remain undetected increases the damage they can cause – more systems compromised, more data stolen, and deeper network penetration.
Verizon’s 2024 analysis of over 30,000 security incidents revealed that ransomware accounted for 23% of breaches, with many attacks succeeding because security teams lacked visibility into initial infection vectors.
Third-Party and Supply Chain Complications
Organizations increasingly depend on vendors, contractors, and partners who require network access. Split tunneling multiplies the risks associated with these third-party connections.
Vendor Access Points
Third-party contractors often request split tunneling to access their own resources while supporting your systems. This creates multiple attack surfaces that are difficult to monitor and secure.
A compromised vendor using split tunneling can serve as an entry point for attackers targeting your organization. Supply chain attacks have increased significantly, with 15% of breaches involving third-party infrastructure.
Vendors may have weaker security practices than your organization. Their compromised systems can pivot through your network when connected via split-tunneled VPNs.
Limited Oversight and Control
You can’t directly monitor or control the security posture of third-party networks. When vendors use split tunneling, their unencrypted traffic can include malware downloads or compromised applications.
Business Associate Agreements and vendor security requirements become harder to enforce with split tunneling. You lose visibility into whether vendors are following agreed-upon security practices.
Understanding how VPN encryption protocols and security features work is essential for implementing robust access controls and proper network segmentation.
Enterprise Security Solutions That Actually Work
Organizations don’t have to accept split tunneling risks as inevitable. Several technologies and approaches can provide performance benefits without creating security vulnerabilities.
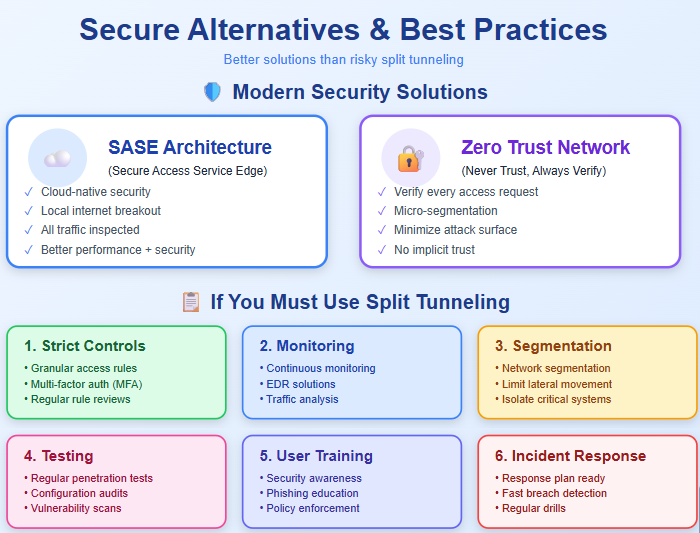
Secure Access Service Edge (SASE) Architecture
SASE combines network security functions with WAN capabilities to provide secure access regardless of location. It delivers security as a cloud service rather than forcing all traffic through centralized data centers.
Modern SASE solutions from vendors like Palo Alto Networks and Zscaler route traffic intelligently while maintaining security controls. Users get local internet breakout for better performance, but all traffic remains inspected and protected.
Zero Trust Network Access Principles
Zero Trust architecture assumes no user or device should be trusted by default, regardless of location. Every access request is verified before granting permission.
Implementing Zero Trust principles minimizes the attack surface that split tunneling would otherwise create. Even if traffic flows outside traditional VPN tunnels, Zero Trust controls authenticate and authorize each connection.
This approach is particularly effective for protecting cloud resources and SaaS applications that users frequently access through split-tunneled connections.
For additional context on managing remote access security, read our analysis of government tracking of VPN users and privacy implications.
How to Minimize Split Tunneling Risks
If your organization determines that split tunneling is necessary, specific measures can reduce the associated risks. Implementation requires technical expertise and ongoing management.
Strict Access Controls and Monitoring
Define granular rules that specify exactly which applications or destinations can use split tunneling. Review and update these rules regularly as your environment changes.
Implement continuous monitoring of all network connections, whether tunneled or not. Deploy endpoint detection and response (EDR) solutions that can identify suspicious behavior regardless of network path.
Require multi-factor authentication for all VPN connections. CISA’s security recommendations emphasize the critical importance of MFA in preventing unauthorized access.
Network Segmentation and Microsegmentation
Limit the lateral movement possible if a split-tunneled device becomes compromised. Segment your network to isolate critical systems and sensitive data from general corporate resources.
Microsegmentation takes this further by creating fine-grained security zones around individual workloads. Even if attackers breach the network through a split-tunneled connection, segmentation limits how far they can move.
For organizations seeking to improve their overall security posture, learning about VPN security features and encryption standards helps inform better configuration decisions.
Regular Security Audits and Testing
Conduct penetration testing specifically targeting split tunneling configurations. Security teams should attempt to exploit these connections to identify vulnerabilities before attackers do.
Review split tunneling policies quarterly at minimum. Assess whether each exception remains necessary and appropriately secured.
Test all routing rules across different devices, operating systems, and use cases. Comprehensive testing is essential to catch errors before deployment.
User Education Makes the Difference
Technical controls alone can’t eliminate split tunneling risks. Users must understand the dangers and follow security best practices.
Security Awareness Training
Employees need to understand what split tunneling is and why it creates risks. Training should cover specific scenarios where split tunneling could expose data.
Teach users to recognize signs of compromise – unusual network activity, unexpected popups, or systems behaving strangely. Quick reporting can minimize damage from breaches.
Make security training practical and relevant. Use real examples from your industry to demonstrate how split tunneling vulnerabilities lead to actual breaches.
Acceptable Use Policies
Document clear policies about split tunneling usage. Specify when it’s permitted, which devices can use it, and what activities are prohibited.
Acceptable Use Policies should be signed by all employees and contractors, with consequences for violations clearly stated.
Regular reminders help maintain security awareness. Don’t just train once – make security a continuous part of your organizational culture.
The Future of Remote Access Security
The cybersecurity landscape continues evolving rapidly. Organizations must adapt their security strategies to address emerging threats while maintaining productivity.
Emerging Technologies and Standards
CISA’s 2024-2026 Cybersecurity Strategic Plan emphasizes the importance of building security into technology products by default – the “Secure by Design” principle.
New standards and frameworks are emerging to help organizations secure remote access without the trade-offs that split tunneling requires. Following industry best practices and government guidance will become increasingly important.
Balancing Security with Usability
The fundamental challenge remains – users need convenient access to resources without compromising security. The solution isn’t accepting unnecessary risks but implementing proper security architecture.
Organizations that invest in modern security solutions like SASE and Zero Trust will find they can provide better user experiences while actually improving security compared to traditional split-tunneled VPNs.
Technology continues advancing. What seemed like the only option yesterday may have better alternatives available today. Regularly reassess your remote access strategy.
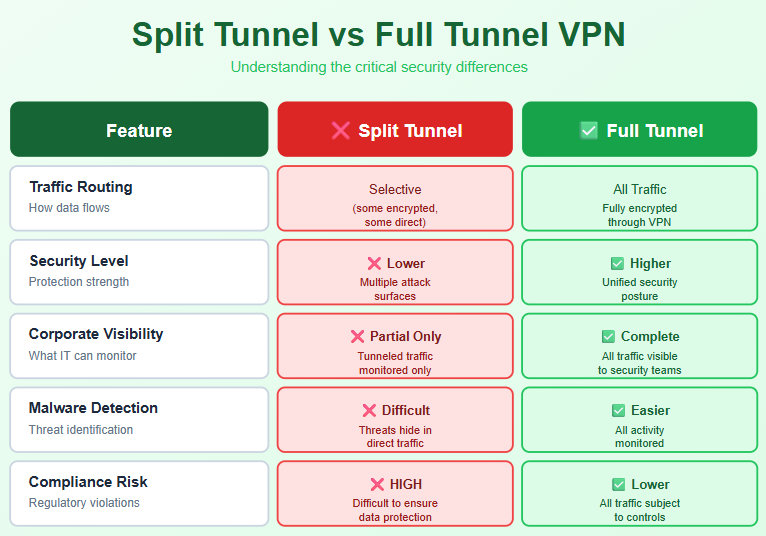
Comparison: Split Tunneling vs. Full Tunnel VPN
| Feature | Split Tunneling | Full Tunnel VPN |
|---|---|---|
| Traffic Routing | Selective (some encrypted, some direct) | All traffic encrypted through VPN |
| Corporate Visibility | Partial – only tunneled traffic monitored | Complete – all traffic visible to security |
| Performance | Better for bandwidth-heavy apps | May experience latency with large files |
| Security Level | Lower – creates multiple attack surfaces | Higher – unified security posture |
| Compliance Risk | High – difficult to ensure all regulated data protected | Lower – all traffic subject to controls |
| Configuration Complexity | High – requires detailed rules management | Low – simple all-or-nothing approach |
| Malware Detection | Difficult – threats can hide in direct traffic | Easier – all activity monitored |
| Home Network Risk | High – compromised home network affects corporate | Lower – traffic isolated from local threats |
Source: Based on security analysis from multiple cybersecurity frameworks (2024-2025)
Conclusion
Split tunneling creates serious security vulnerabilities that most users and organizations don’t fully understand. While it offers performance benefits, those advantages come at the cost of reduced security visibility, bypassed protection mechanisms, and increased risk of data breaches. Organizations should carefully evaluate whether split tunneling is truly necessary or if modern alternatives like SASE and Zero Trust can provide better performance without compromising security. If split tunneling is unavoidable, implement strict access controls, comprehensive monitoring, and regular security audits to minimize risks. The future of remote access security lies in solutions that eliminate the need for such trade-offs entirely.
Frequently Asked Questions
Q: Can split tunneling be used safely in corporate environments?
Split tunneling can be somewhat safer with strict controls – granular access rules, continuous monitoring, endpoint protection, and network segmentation. However, it still introduces risks that full-tunnel VPNs or modern SASE solutions avoid entirely. Organizations in regulated industries should generally avoid split tunneling due to compliance concerns.
Q: How can I tell if my VPN is using split tunneling?
Check your VPN client settings for options labeled “split tunneling,” “selective routing,” or “exclude from VPN.” You can also test by connecting to your VPN and checking if your IP address differs between various websites. If some show your real IP while others show the VPN IP, split tunneling is active.
Q: Does split tunneling make my personal browsing faster while working remotely?
Yes, split tunneling can improve speeds for personal activities like streaming or gaming by routing that traffic directly through your ISP. However, this convenience exposes you to security risks including malware infections, data interception, and potential compromise of both personal and corporate data. The performance gain isn’t worth the security trade-off in most cases.
Q: What’s the difference between split tunneling and having no VPN at all?
Split tunneling protects traffic routed through the VPN tunnel while leaving other traffic unencrypted. No VPN means all traffic is unencrypted. The danger with split tunneling is that users may not realize which applications are protected versus exposed, and infected devices with split tunneling can still compromise corporate networks through the VPN connection.
Q: Are there industries where split tunneling should never be used?
Healthcare, financial services, and government sectors handling classified information should generally avoid split tunneling due to strict regulatory requirements like HIPAA, PCI-DSS, and FedRAMP. These industries face severe penalties for data breaches and typically can’t meet compliance standards with split tunneling enabled. Even a single compliance violation can result in millions in fines and reputational damage.
Loading newsletter form...






